Profit-making is the ultimate aim behind any work that an individual performs. In regard to that, MEV, which stands for Maximal Extractable Value, signifies the profit a validator makes from a smart contract-enabled blockchain for including, excluding or re-ordering transactions in the blocks.
In short, MEV represents the measure of profits that a miner/validator could extract for reviewing transactions on the blockchain network. More in detail about MEV- the good and bad, insights into safeguarding the funds from MEV tricks will be the highlights of this blog.
What Is MEV? How Does It Work?
In proof-of-work consensus, the miners were responsible for adding transactions, previously called Miner extractable value. But with Ethereum’s shift to Proof-of-stake, validators are the ones who assess the transactions it got changed to Maximal Extractable Value(MEV).
Generally, the user pays a fee in the blockchain for moving around transactions in a block. That fee amount is an additional charge that the user prefers to pay for miners to choose their transaction on priority.
This MEV amount which is nothing but the gas fee paid by the user is filtered in the order of the highest amount by the validators to make it more profitable for them. Bots are used to automate the process of submitting profitable transactions with high gas fees that incentivize validators.
Despite this practice of prioritizing transactions based on the gas fee paid, MEV also introduces several other effects on the blockchain. We shall see how MEVs are manipulated to draw benefits in the upcoming passage.
How are MEVs used tactically?
Validators and hackers trying to find opportunities by exploiting MEV put users in economic distress. But what are the ways these MEVs are used to the hacker’s advantage?
Let’s dig into the details now!
Front-running: All the transactions which need to be validated sit in the mempool, wherein validators or generalised front-runners(bots) run through them and go with the profitable trades. Since the code is open on the blockchain, bots detect the user’s transaction with high gas fees, replicate them and help validators find the profitable ones.
This way, the transaction orders are communicated for them to be preferentially added to blocks.
Sandwich attack: Here comes the malicious form of front-running wherein the user’s transaction is studied to manipulate the prices of cryptocurrencies and perform trading to the hacker’s advantage at the expense of users.
To simplify it, let’s assume a price difference of a specific crypto coin between the DEXs, Uniswap and Sushiswap. The user finds this and tries to profit by buying the asset from Uniswap for a lower price and selling it on Sushiswap at a higher price.
This way, the liquidity of cryptocurrencies is maintained across different decentralized exchanges. But here is where the problem is. Once the user initiates the transaction for the buy and sells orders, they stay in the mempool for it to be validated.
Meanwhile, the bots identify this potential opportunity for gaining profits and replicate the same transaction with a high gas fee.
As a result, the buy order of the bot is executed before the user, pumping the token price.
The user’s buy order is processed after, and the user buys the token at a high price.
The bot then initiates the sell order of the asset at the increased price, deriving wholesome profits at the knowledge of the user, who ends up deprived of the money they intended to make.
The price that the MEV victim pays due to manipulation is the amount of “Slippage” they’ve entered while making the transaction.
P.S. Slippage is the price difference between the time of trade initiation and execution.
A user can buy the tokens at a lower price from one DEX and sell them on a high-priced DEX in a single transaction by swapping tokens.
DEX arbitrage: DEX arbitrage is one of the most well-known MEV opportunities whereby users can extract profits from the price differences between two DEXs.
Liquidations: Lending protocol liquidations present MEV opportunity to make earnings out of the liquidation fee. DeFi lending protocols allow users to deposit some cryptos as collateral and, in return, borrow the crypto tokens they need.
If the user cannot repay the borrowed funds, the protocol allows anyone to liquidate the collateral placed by the borrower, for which a hefty liquidation fee is charged. This liquidation fee goes to the liquidator.
It is utilised by MEV searchers who hunt down borrowers whose assets can be liquidated and earn profits from the liquidation fee.
Bright Side And Dark Side of MEV
The bright side of MEV argues its role in smoothing the liquidation process across various decentralized exchanges ruling out economic inefficiencies.
Moreover, organizations like Flashbots provide products to offer front-running as a service to instil a permissionless and transparent MEV ecosystem.
On the downside, front-running and sandwich attacks are causing more expensive revenue loss and lost arbitrage opportunities for the users. MEV bots make it rough for newcomer traders to participate in DeFi protocols which detriments the security aspect.
In addition, generalized front-runner bots replicating transactions with high gas fees create network congestion and increase the transaction fee, affecting the user.
Drawing Out The Recent MEV Bot Hack Scenario
Attack Plot: The MEV bot OxBAD made ~$150k from $11 by front-running a transaction. Soon after the token swap to make profits, the MEV bot’s bad code was exploited in the following transaction https://t.co/FxXSY8AyhX, draining 1,101 ETH.
Into The Specifics Of Hack…
MEV bot made a successful attempt in front-running a trade of $1.8 million swap from cUSDC to some other stablecoins. This resulted in the user ending up with only $500 worth of assets in return.
However, soon after that, the MEV bot named Oxbad was tricked by an exploiter to lose the gained profit.
On looking at the hack, the exploiter leveraged the bot’s callback routine to approve arbitrary spending leading to a 1,101 ETH loss.
High On Hacks
Other exploits in the row around the same time in Sept’22 were
- A bug detected in the Profanity tool, an Ethereum vanity address generator, resulted in draining $3.3 million in funds from various wallets.
- A week later, a vanity wallet address was hacked, with a loss estimated to be around $1 million worth of ETH.
Getting at Security Practices to Follow
Private mempools: Generally, transactions stay in the mempool where they are publicly broadcasted for the miners/validators to pick and add them to blocks. In private mempools, transactions are only visible to the pool and not displayed to other nodes, which cuts down the chances of MEV cost.
Example: Taichi Network, BloXroute.
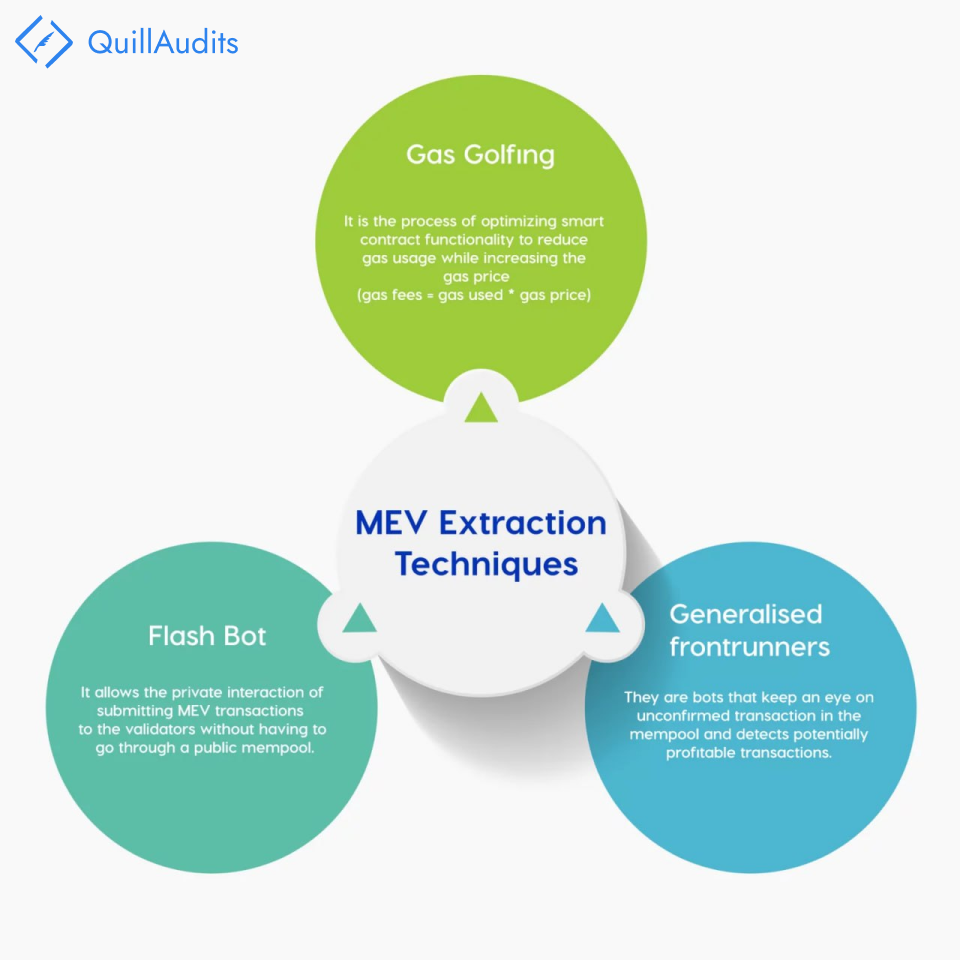


Flash bots: Flashbots is a research organisation which works to address the conflicts of MEV by democratizing MEV extraction through MEV-Geth. MEV-Geth provides a private block space auction mechanism wherein bots and miners can communicate on the transaction order preference.
This reduces the overall gas cost for users and failed transactions bloating the blockchain.
Slippage: Users can enter minimum slippage value while proceeding with the transactions. So that if the price difference exceeds too much, the transaction stands cancelled automatically. This way, the users can be saved from big losses.
QuillAudits In Web3 Security
There are continuing threats right from the code level that crumbles Web3 security. QuillAudits does extensive research on the attack vectors on Web3 and debugs errors offering protection to projects and users’ funds.
Get to know the diversified security services provided by QuillAudits and get yourself shielded from the Web3 hassles.






















