Exploring the security aspect of web3 for enterprises.
Web 3.0 – A Security Advantage
With so many advantages, we are sure that Web 3.0 is going to be the most worked-upon technology in the near future, and one of the main reasons for that is the security we are provided with the flexibility of Web 3.0.
You cannot give an axe to a child. Similarly, you can only create in Web 3.0 with skilled developers. Regarding the security aspect of your business, you need experts like QuillAudits to help you get the most out of security. Now, let’s explore some approaches and solutions that help Web 3.0 security models outshine the previous Web versions.
Unconventional Approaches to Web3 Security for Enterprises
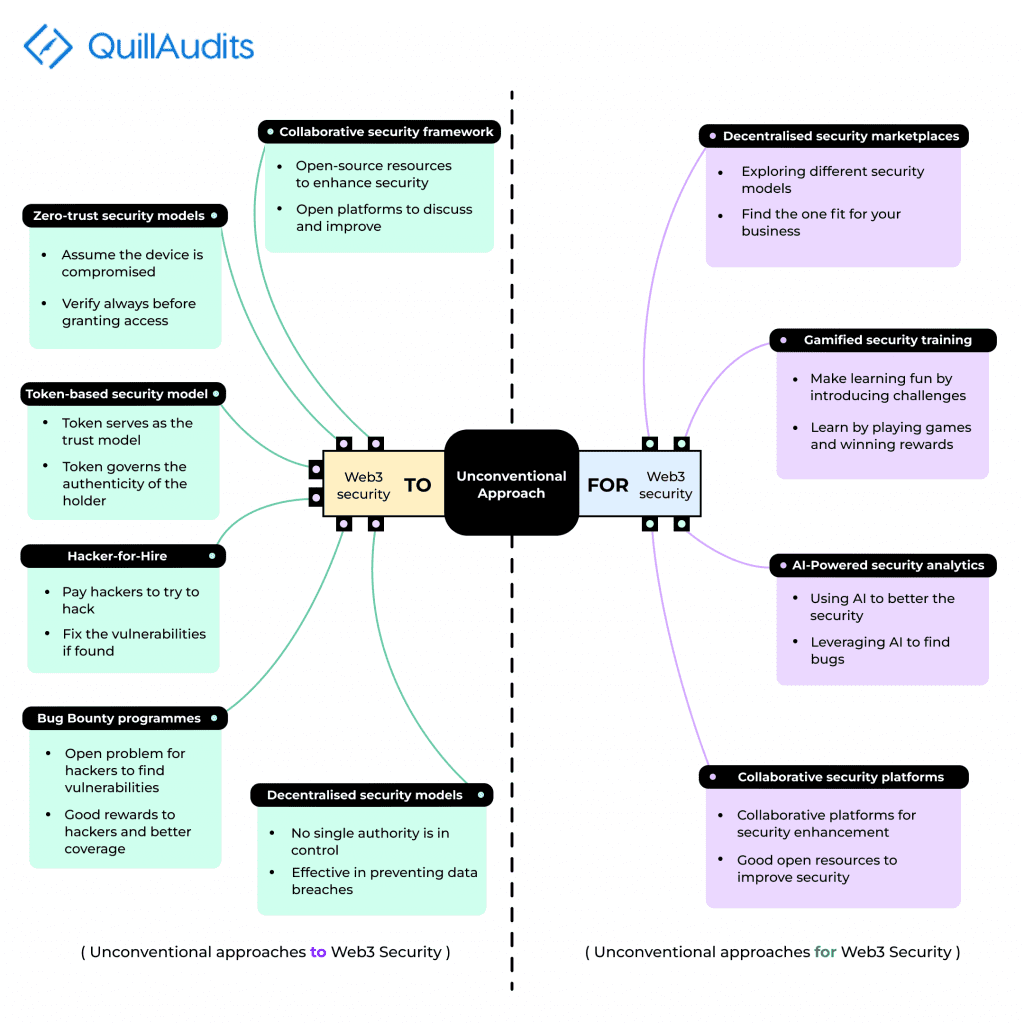


Zero-trust security models
This model assumes that any user or device attempting to access the network may be compromised and must be verified before granting access. And Web3 features such as blockchain technology and decentralised applications play a role in zero-trust methodology by providing additional layers of security and transparency.
Collaborative security frameworks
The Web3 community provides collaboration for security-oriented development. Web3 is majorly open source which helps you tackle security-related issues by learning from the mistakes and findings of others publically available over the internet.
Decentralised security model
Decentralised security makes information security everyone’s responsibility, not just a single central authority. It helps build a strong culture of security and data protection across organisations. It is very efficient in preventing data breaches and helps position your business as the one that takes the protection of customers’ data very seriously.
Hacker-for-hire programmes
This is one of the ways Web3 businesses safeguard their users by hiring a hacker to try to hack into their business. If any vulnerability or issue is found, it is fixed with the help of developers.
Bug Bounty programmes
This is similar to the hacker for hire, but the only difference is the choice of hacker and reward for the hacker, in this the challenge is laid out in the open, saying that who so ever can find a vulnerability in the business protocol will be awarded based on the seriousness of the vulnerability, This way there is a more outreach in terms of testing as compared to Hacker for hire programme.
Token-based security model
The security token works like an electronic key to access something. It can be opening unlocked doors or a banking token used as a digital authenticator. Basically a token of trust which guarantees the authenticity of the holder.
Unconventional Solutions for Web3 Security in Enterprises
We saw different approaches we were gifted with when we worked on Web3-related projects. This part of the blog will introduce you to different solutions and ways we can empower Web3 for security and discuss a few possibilities along with some already existing methods.
Collaborative security platforms
Being such an awesome community Web3 is, it has its perk to be a part of. It is not hard to imagine people from across the globe all sharing security-related stuff on a platform, learning, developing, and creating a more secure future. This is where Web3 stands apart from others, It’s the community, and here we collaborate well, and a platform where all security-related details shared among peers is not a foreign concept in Web3. Especially if you are a part of QuillAcademy 🙂
Decentralised security marketplaces
Imagine a platform with different types of decentralised security models we can choose from for our organisation as we see fit. For example, let’s say we want to create a decentralised security system for sales data. Here we can employ such security models where the people from sales, marketing and HR department can access it with the distribution of security to different departments, which are related to it, and the security enhanced.
Gamified security training programs
Nowadays, learning is associated with fun, and playing games have always been fun, so why not have fun while learning? This is no new concept. It’s the same concept we use with children. We make studying fun so that children adapt and consume faster, the same we can do with the security training programmes and a step in that direction leads us to CTF’s. QuillAudit has some world-class CTF problems; check them out on the website.
AI-powered security analytics
When it comes to new revolutionary technologies, how can we not talk about AI? Powering many sectors of today’s world. It can be used for powering the security aspects of the web. Continuous research and development are being carried out to make this a reality.
Conclusion
With a web3-focused discussion on enterprises in part-1, we learned about many advantages. Web3-based companies will enjoy compared to conventional ones. The human race is today where it is just because some of us followed an unconventional way. Now is the time to do it again.
The web3 security-based discussion on approaches and solutions has brought to light many opportunities waiting to be explored under the security umbrella. Why hesitate? It’s the perfect time to get started. I am sure the first mover’s advantage is still a thing.
Lastly, let’s thank the one who made this blog possible for you. We QuillAudits, bring you the latest security-related updates, fixes and educational content so that you can stay ahead of the security game and help us make web3 a safer world. Don’t forget to visit our website and register for an audit if you are building in web3. Trust me; Some projects would have saved millions if they had done that






















