Introduction
In 2022, Epic Games CEO Tim Sweeney expressed that zero-knowledge proofs (ZKPs) would be a crucial aspect of blockchain technology in the future. ZKPs allow us to prove the truth of something through cryptography without disclosing additional information. They offer strong privacy and scalability, as we only need to share a cryptographic proof of relevant data instead of our actual data. This proof can be reliably verified without risking the exposure or misuse of personal information.
By using ZKPs, we can interact with online services and provide them with relevant information for specific actions without revealing unnecessary details. In the context of blockchain networks, ZKPs allow one party to prove to another that they possess knowledge about certain information without revealing the actual information itself.
The Benefits of ZK-Proofs for Blockchain
- Scalability: With zk-SNARKs or zk-STARKs, only one person does the computation, and others verify proof for slow-verifying blocks.
- Privacy: ZK enhances privacy in transactions by validating information like balance without exposing unnecessary details, e.g., sender’s identity.
zk-SNARK Stands for Zero Knowledge – Succinct Non-interactive Argument of Knowledge. In addition to the privacy advantages previously mentioned, they are notable for being “succinct,” which means the proofs are small (288 bytes) and they can be verified very quickly. This has efficiency and decentralization benefits since succinctness makes it simpler for everyone to verify and take part, not just those with sophisticated computer setups capable of handling the pricey computations that are needed for the majority of traditional blockchains.
ZK-STARKs, a type of zero knowledge proof, are preferable when dealing with large witnesses. They offer higher transparency and do not require a trusted setup, using publicly verifiable randomness instead. Although ZK-STARKs have a higher verification overhead compared to zk-SNARKs, they are more cost-effective for scaling purposes.
Breaking Down zk-SNARKs: How Do They Even Work?
zk-SNARK (zero-knowledge Succinct Non-interactive ARgument of Knowledge) is a zero-knowledge proof method enabling one party to verify a statement’s truth to another without disclosing the statement’s details.
Non-interactive proof allows the prover to convey the proof to the verifier without additional interaction. Zero-Knowledge guarantees that only the statement’s validity, not extra details, is disclosed. Succinctness highlights the compactness and quick verification of zk-SNARKs, needing minimal computational resources.
How do zk-SNARKs work?
A representation of the three functions of a zk-SNARK proof. Source.
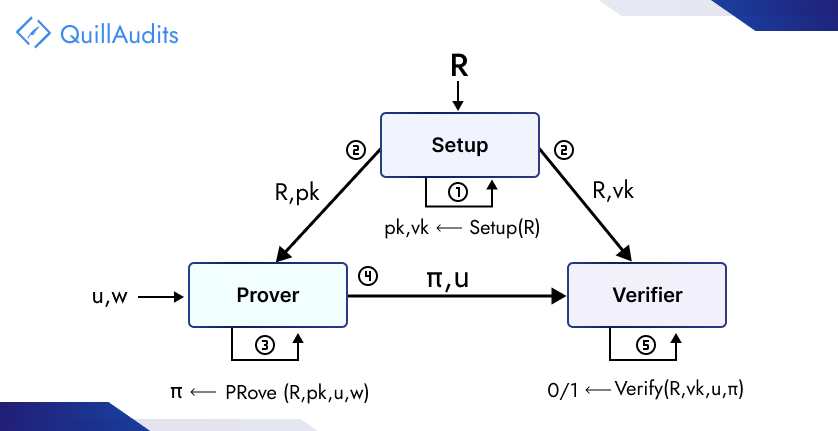


zk-SNARKs involve three essential steps: key setup, proof creation, and verification, each utilizing specific variables integral to the cryptographic process.
1. Key Setup
- In this phase, cryptographic keys are generated for the proof system: a proving key (pk) for creating proofs and a verification key (vk) for checking them. This setup uses a security parameter (λ) and a representation of the statement to be proven, which includes public (x) and private (w) inputs.
- The setup function is denoted as: (Setup(C, λ) → (pk, vk))
2. Proof Creation
- Here, the prover uses their private input (w), the public input (x), and the proving key (pk) to generate a proof (prf). This proof demonstrates their knowledge of (w) without revealing any information about it.
- The proof generation function is expressed as: (Prove(w, x, pk) → prf)
3. Verification
- In the verification step, the verifier uses the verification key (vk), the proof (prf), and the public input (x) to determine the proof’s validity. The result is either True, indicating the proof is valid, or False, if it is not.
- The verification function is represented as: (Verify(vk, prf, x) →) True or False
These steps and variables form the core of zk-SNARKs, facilitating a secure and efficient cryptographic proof system.
Key Features of ZK-SNARKs:
- They offer great data availability with scalable performance.
- Enable computations without interaction.
- Security relies on initial setup; any mistake impacts all applications and could lead to incorrect proofs.
- Known for their small proof sizes and reliable verification speed, which helps reduce costs in ZK-rollups on primary networks.
And Then There are zk-STARKs: What’s the Deal with Them?
zk-STARKs represent a breakthrough in privacy and scalability for cryptographic systems, eliminating the need for a trusted setup thanks to publicly verifiable randomness.
Simply put, zk-STARK stands for Zero-Knowledge Scalable Transparent Argument of Knowledge. This technology allows for the verification of data or calculations without revealing the underlying information to another party.
Previously, zk-SNARKs were used for similar purposes, but they required a trusted setup, which posed a risk to system privacy if the setup parties were compromised. zk-STARKs improve upon this by removing the need for such a setup.
STARKs also address scalability and privacy concerns on open blockchains. StarkWare Industries, a leader in STARK technology, focuses on enhancing scalability first, with privacy improvements to follow.
STARKs boost scalability by allowing computations and data storage to be moved off the main chain. Off-chain services can generate STARK proofs to verify computations’ correctness, which are then published back on the blockchain for public verification.
This approach significantly reduces the computational load on the blockchain itself, enabling it to handle much larger volumes of transactions without sacrificing security or integrity.
In practical applications, layer-2 solutions utilize STARKs to process and validate thousands of transactions in a single batch on-chain, drastically reducing the gas cost per transaction. StarkWare is at the forefront of integrating Zero-Knowledge Scalable Transparent Argument of Knowledge into various blockchain platforms, including Ethereum, to achieve these benefits.
Key features of ZK-SNARKs:
- Eliminates the requirement for a trusted setup at the beginning.
- Highly scalable, with proof creation and verification times growing more gradually than in zk-SNARKs, even with large volumes of data.
- Increased proof sizes lead to higher costs for verification.
- Offers protection against potential quantum computing attacks.
zk-SNARKs vs. zk-STARKs, What Sets Them Apart?
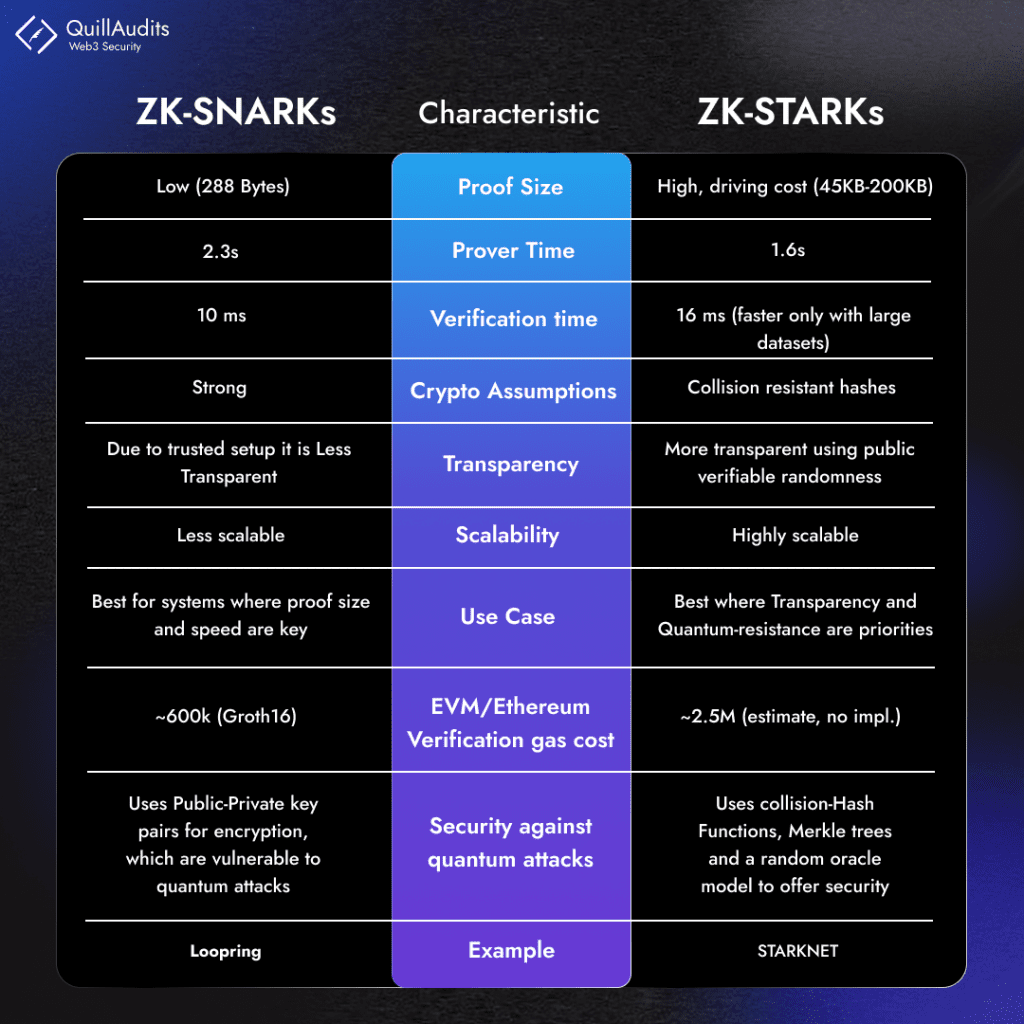


- Data Availability: zk-SNARK is more popular, especially in L1 rollups, due to its advantage in data availability over zk-STARK.
- Security: zk-SNARKs require a trusted setup involving a Common Reference String (CRS), which could be compromised. zk-STARKs, on the other hand, are quantum-resistant and less vulnerable to threats as they don’t rely on such setups.
- Transparency: zk-STARKs are inherently more transparent than zk-SNARKs, as they depend on public randomness for parameter establishment, while zk-SNARK’s trusted setup may be perceived as less transparent.
- Scalability: zk-STARK is a technology aimed at enhancing blockchain scalability. It doesn’t demand significantly higher computational power compared to SNARK, even for complex proofs, implying better scalability. The graph below, derived from the STARK whitepaper, demonstrates that STARK exhibits relatively minor variations in time requirements as proof complexity increases.
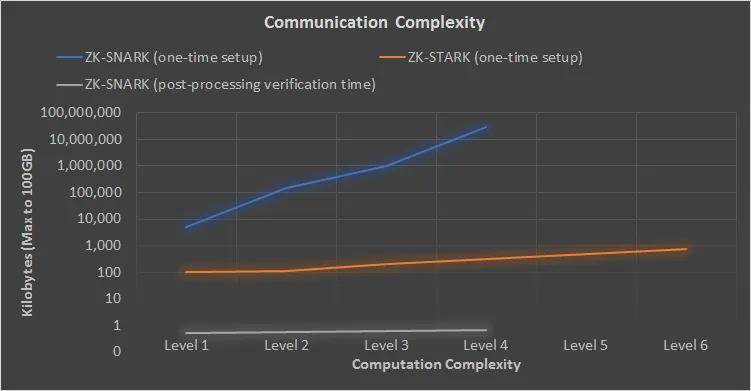


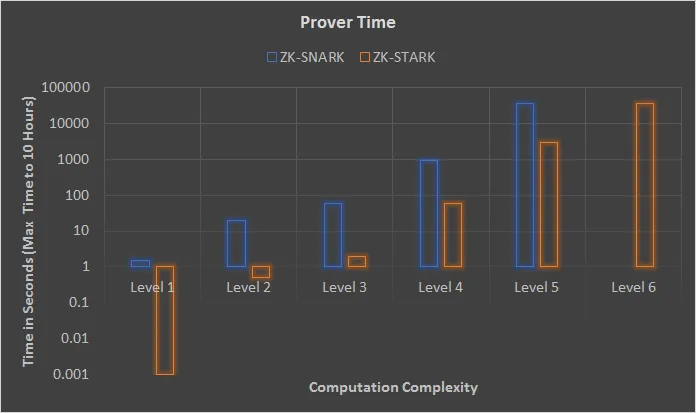


As the computational complexity increases, the time required for Snark increases significantly compared to Stark
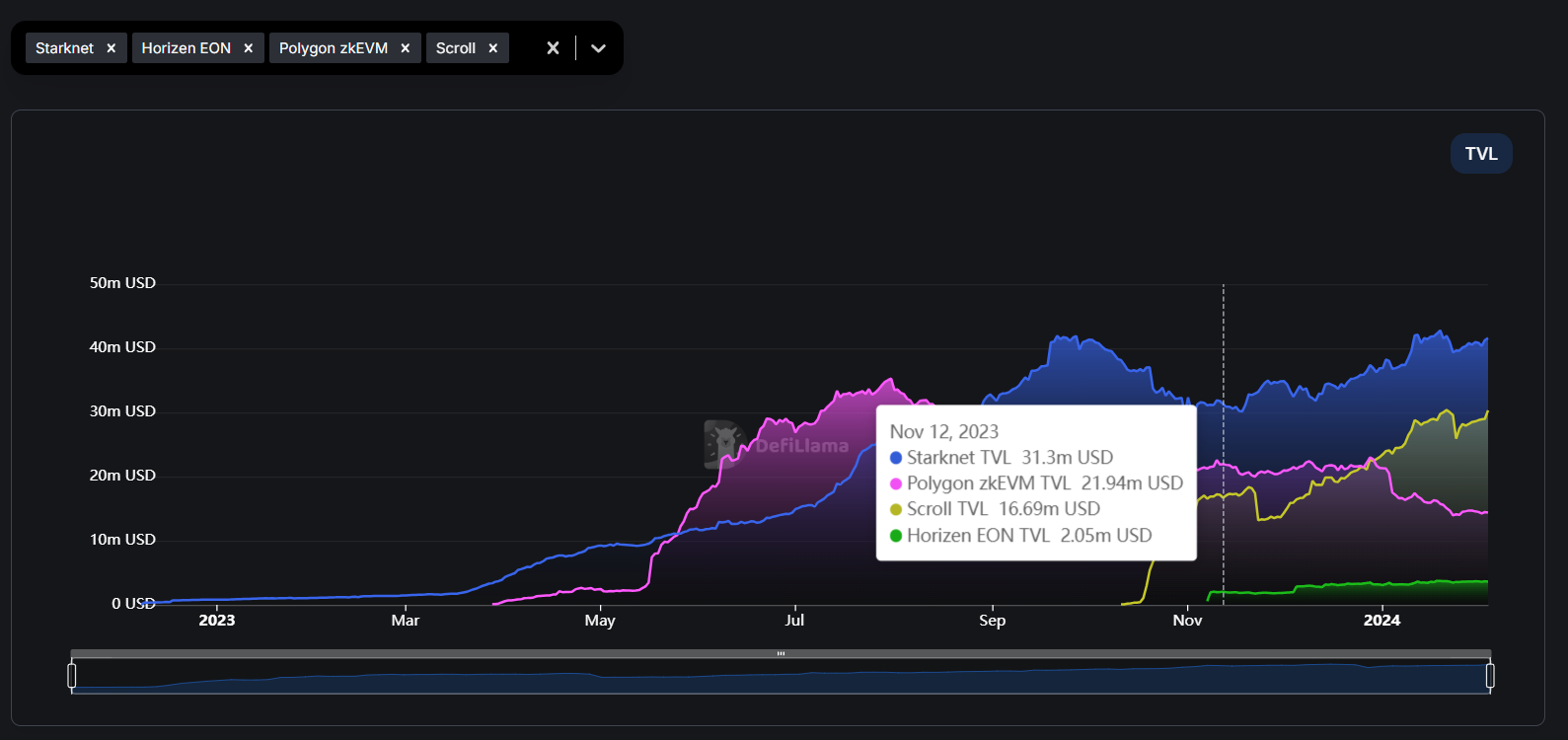


Comparison of Different chains on both zk-snark and zk-stark technology.
zk-SNARKs vs zk-STARKs in the Real World:
In this section, we will explore real-world applications that make use of zero-knowledge proofs, specifically zk-STARKs and zk-SNARKs. Discover how these cryptographic tools open up new possibilities:
zk-STARKs
- StarkWare’s StarkEx leverages zk-STARK technology to increase transaction efficiency and reduce gas fees on Ethereum.
- dYdX uses StarkEx’s zk-STARKs for private, cost-effective leveraged trading and other financial instruments.
- Immutable X employs zk-STARKs for instant, scalable, and gas-free NFT transactions, maintaining user custody.
zk-SNARKs
- Scalability: zk-Rollups use zkSNARKs for efficient blockchain scaling, reducing transaction costs and increasing speed. Example: Polygon Hermez, zkSync.
- Privacy transactions : zkSNARKs enable private transactions, hiding transaction details while ensuring verifiability. Example: Z-Cash, Tornado Cash.
- Identity Protection: zkSNARKs allow secure verification of credentials without revealing personal data, mitigating identity theft. Example: zk-creds protocol.
Wrapping Up: What Have We Learned?
From the discussion, it seems that STARKs are shown in a better light than SNARKs when comparing them. STARKs offer greater scalability, openness, and security for blockchain systems. However, it’s important to note that STARKs have larger proof sizes and their verification takes more time.
Therefore, if a developer begins to use zero-knowledge tech, SNARKs might get more support due to their advantages. SNARKs are also expected to consume less gas by about 24%, making transactions cheaper for users. Meanwhile, STARKs are still new and need more time to demonstrate their effectiveness to developers and others in the blockchain community.
Resources
- Buterin, V. (2022). “Some ways to use ZK-SNARKs for privacy.”
- Zero-Knowledge-Mastery
- Zero-Knowledge Proof in Blockchain Explained | Quillaudits
- STARK Paper
FAQs
- What are zk-Rollups ?
zk-Rollups are a blockchain scaling solution that bundles (or “rolls up”) multiple transactions into a single transaction. They use zero-knowledge proofs (zk-proofs) to validate the bundled transactions, enabling faster processing and reduced transaction fees on the main blockchain.
- What is a merkle tree ?
A Merkle tree is a data structure in cryptography that summarizes all the transactions in a block into a single digital fingerprint, allowing for efficient and secure verification of large data sets.
- What is the collision-resistant hash function ?
A collision-resistant hash function in zk-STARKs is a secure hash function that prevents finding two distinct inputs that result in the same output, ensuring the reliability of zk-STARKs’ cryptographic proofs.
- What is public randomness ?
Public randomness in ZK-STARKs refers to the use of publicly verifiable random values in the cryptographic process. These values help in generating proofs that are both transparent and secure, ensuring that the verification process can be trusted by anyone without revealing any private information.






















