The concept of decentralization in DeFi may mask the real risks that both experienced and new investors might encounter. Smart contracts, critical to DeFi platforms, are self-executing contracts with the terms directly written into code. While they enhance efficiency and transparency, their permanent nature means that any code errors could lead to irreversible outcomes. Therefore, it’s essential for anyone entering the DeFi space to understand and address these risks.
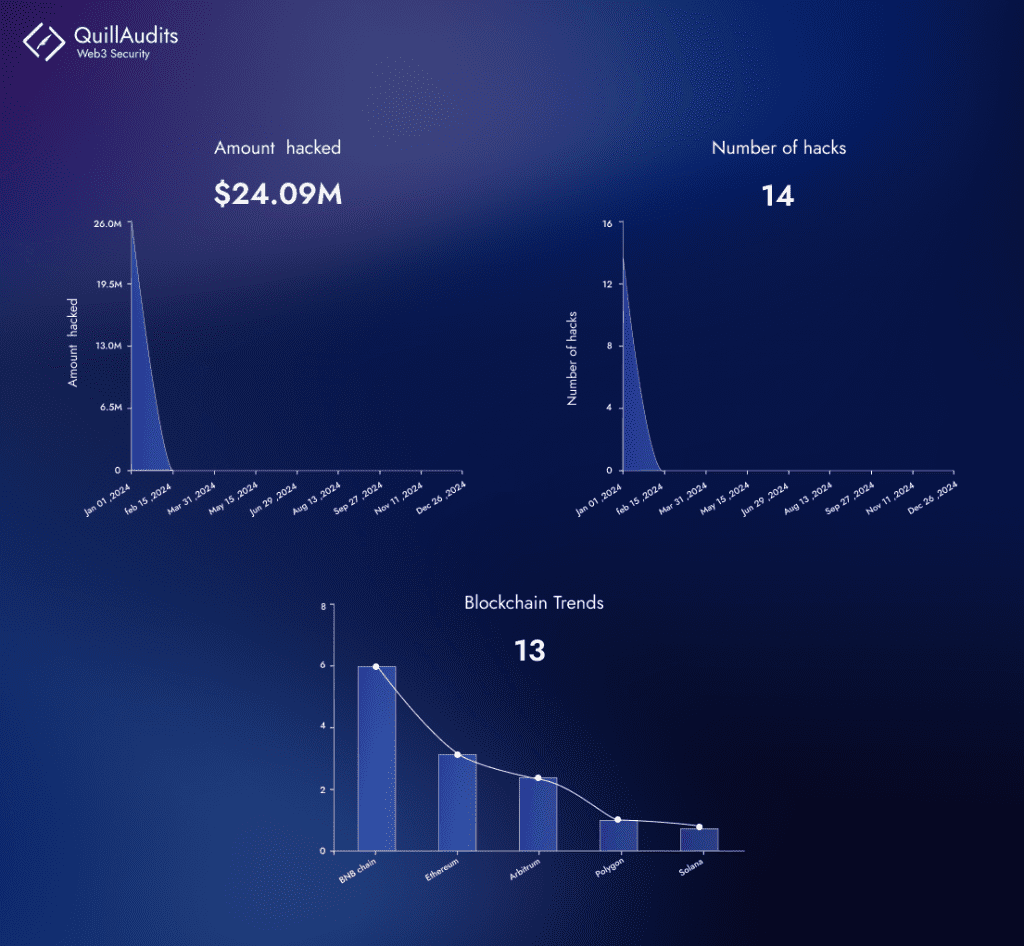
Especially noteworthy as we begin 2024 is the significant loss of over $25 million in crypto hacks tied to various DeFi risks. Smart contract security is crucial in DeFi, as these immutable contracts dictate the execution of transactions without intermediaries. Given their permanence, any vulnerabilities can have lasting impacts, making rigorous audits and security practices essential. For investors, understanding these security measures is key to navigating the DeFi landscape safely, emphasizing the need for a balance between innovation and risk management in this rapidly evolving sector.


Smart Contract Vulnerabilities
Reentrancy Attack
Reentrancy is a smart contract vulnerability allowing untrusted external code execution inside, often caused by a contract calling another, leading to an infinite loop. This flaw, if exploited, enables an attacker to repeatedly call a function, potentially resulting in fund theft. An example is a contract allowing deposits and withdrawals, where a poorly implemented reentry check could be exploited for unauthorized fund retrieval.
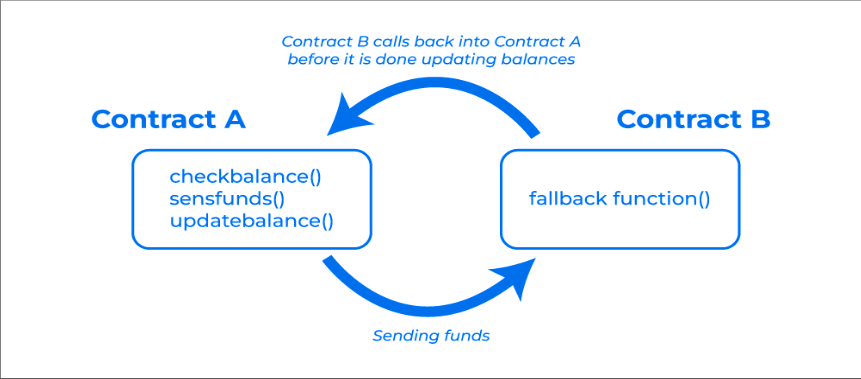


In December 2021, Grim Finance lost $30 million due to a reentry attack where an attacker’s malicious contract exploited the deposit function for multiple investment proofs, leading to significant financial gains. In April 2020, dForce suffered a massive $24 billion loss from an attack leveraging ERC-777 token’s callback feature, which manipulated transaction notifications. The most infamous reentrancy attack occurred in June 2016 against The DAO, resulting in a $60 million loss and accounting for 5.6% of all ETH in circulation, leading to a significant fork in Ethereum into Ethereum Classic and Ethereum. These notable incidents underscore the critical vulnerabilities in smart contract security and the need for robust protective measures.
Integer Overflow or Underflow Attack
Overflow errors in smart contracts occur when values exceed their maximum, resetting to zero, often due to a lack of built-in detection in Solidity. Developers need to use safe math libraries or proper data types like uint256 to prevent this. Conversely, underflow errors happen when values fall below the minimum, cycling to the maximum value. Underflows are easier to exploit than overflows, typically in transactions with unvalidated inputs, highlighting the importance of vigilant coding practices to mitigate such risks.
A clear example of vulnerabilities related to overflow and underflow can be seen in the notorious cryptocurrency Ponzi scheme called PoWH (Proof of Weak Hands Coin). Initially valued at over a million dollars and marketed as a legitimate pyramid scheme, the project suffered a drastic $800k collapse in a single evening due to arithmetic errors. The section of PoWH’s ERC-20 implementation allowing a user to authorize another user for token transfers has a flaw. A malicious user could enable coins from the first account to be sold from a second account, resulting in an unusually high PoWH Coin balance in the second account due to an ensuing (unsigned) integer underflow.
If We consider their code snippet :-
function sell(uint256 amount) internal {
var numEthers = getEtherForTokens(amount);
// remove tokens
totalSupply -= amount;
balanceOfOld[msg.sender] -= amount;
// fix payouts and put the ethers in payout
var payoutDiff = (int256)(earningsPerShare * amount + (numEthers * PRECISION));
payouts[msg.sender] -= payoutDiff;
totalPayouts -= payoutDiff;
}
At first glance you may not notice, but the _from argument is no longer being passed down the chain. Instead, the sell function assumes msg.sender to be the seller. Unfortunately, if sell is invoked by transferTokens it’s possible that msg.sender’s balance is now being drained of coins that it doesn’t own. While that would usually make people upset, if an empty second account used to make this transfer, and only one PoWHCoin is sent, the second account’s balance will underflow to 1.1579E77 or 2^256 — 1. Once in possession of an account with the maximum possible balance, it’s not too difficult to turn into Ethereum. (The actual attacker messed up once, though: they transferred their entire balance into the contract in an attempt to sell it. Unfortunately for them, that underflowed their balance right back around to maximum again.)
Front-running Attack
These attacks represent a significant challenge in smart contract security. Front-running attacks exploit the transaction process on a blockchain’s distributed ledger, where a malicious entity observes a transaction waiting in the mempool after being broadcasted by a user. By submitting their own transaction with higher gas fees, the attacker ensures their transaction is executed first, aiming for financial gain. This tactic mirrors traditional market front-running, where brokers capitalize on anticipated price movements by acting on a client’s major order before it is executed.
Validators, who have the authority to approve transactions, can manipulate the transaction queue—known as the “mempool”—by reordering, including, or excluding transactions to their advantage. This presents a multifaceted challenge for smart contract security, necessitating robust solutions to safeguard against such exploitative practices.
Two vulnerabilities expose this code to theft:
- Public variables:
targetHashandrewardare visible to everyone, making it easy for attackers to find and exploit them. - Predictable logic: The
solvefunction follows a pattern, allowing attackers to copy and submit faster transactions, stealing the reward.
Adding to the risk: Both submission and verification happen in one transaction, leaving it open to “front-running,” where attackers steal solutions and claim the reward before others.
contract FindThisHash {
bytes32 public targetHash;
uint public reward = 10 ether;
address public winner;
constructor(bytes32 initHash) payable {
targetHash = initHash;
require(msg.value >= reward);
}
function solve(string memory solution) public payable {
require(msg.value >= 1 ether);
bytes32 solutionHash = keccak256(abi.encodePacked(solution));
if (solutionHash == targetHash) {
winner = msg.sender;
msg.sender.transfer(reward);
}
}
}
Economic Risks
- Rug Pull
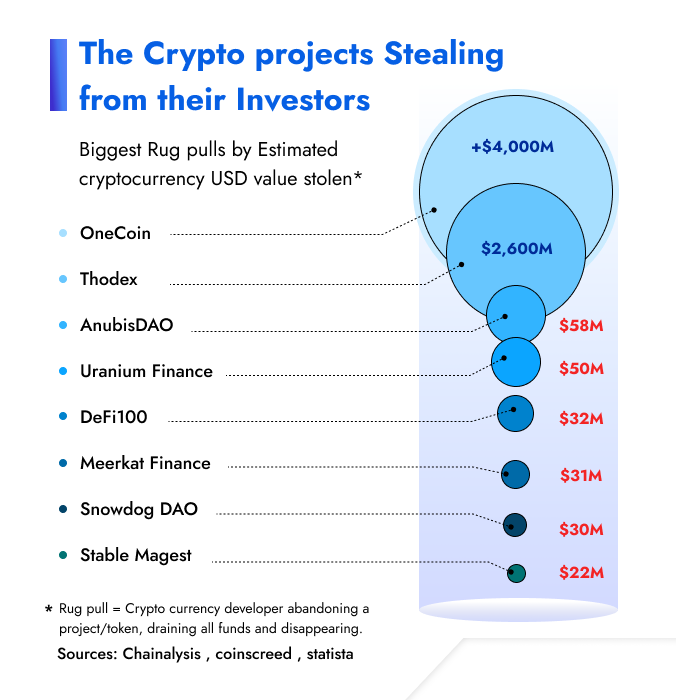
Every cryptocurrency endeavor aims to develop a valuable token, but intentions vary. Genuine projects offer real value, while scams lure investors into funding pools on decentralized exchanges, only to execute a “rug pull” by draining these pools for profit, exploiting the anonymity that the cryptocurrency realm often provides. This anonymity shields scammers from accountability, allowing them to disappear with investors’ money, leaving little recourse for those defrauded.


- Flash Loan Attacks
Flash loan attacks use the momentary liquidity provided by flash loans to manipulate a cryptocurrency’s price, exploit vulnerabilities in a DeFi smart contract, or steal funds from a protocol.
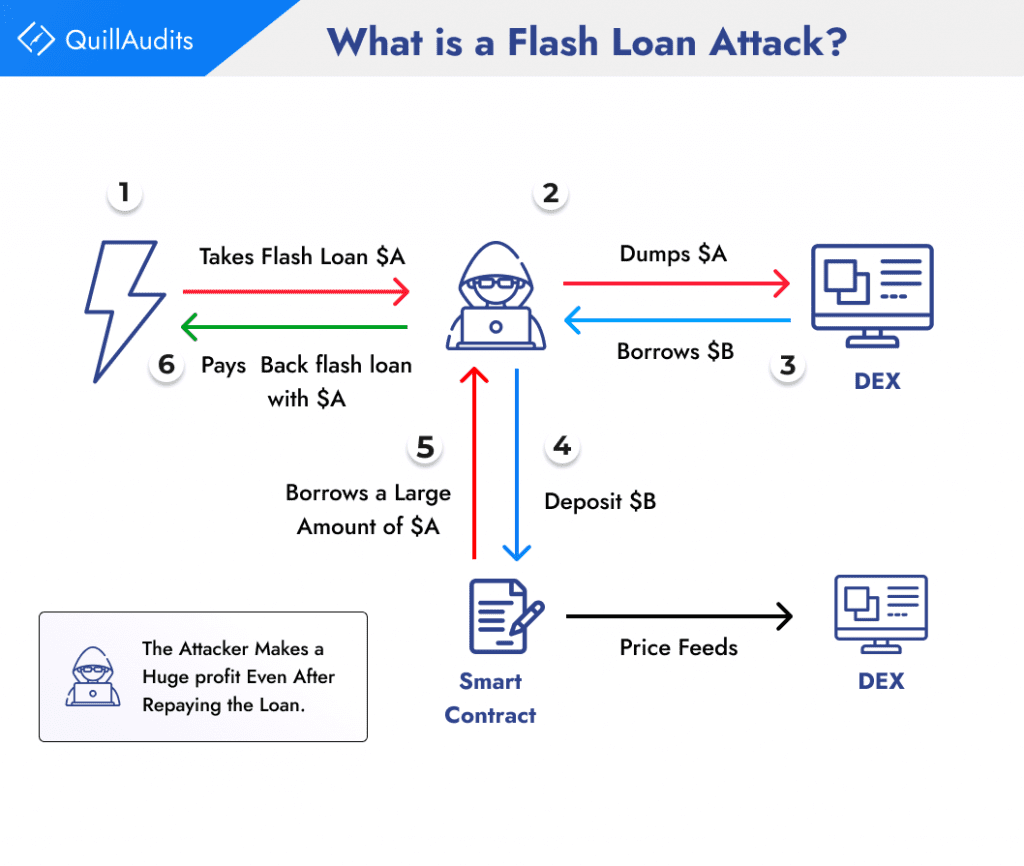


To execute a flash loan attack, an attacker usually follows three steps:
Borrowing: The attacker takes out a flash loan from a DeFi platform, borrowing a large sum of cryptocurrency without providing any collateral.
Manipulating: With the borrowed funds, the attacker manipulates the price of a targeted cryptocurrency or exploits a vulnerability in a DeFi smart contract.
Repaying: The attacker repays the flash loan, typically within the same transaction block, and returns the borrowed funds to the lending platform.
Regulatory Risks:
DeFi encounters a major regulatory challenge because there are no clear and consistent rules worldwide. The uncertainty across different regions makes it hard for DeFi protocols to operate in a compliant way and can also cause market instability. For example, in the United States, the Securities and Exchange Commission (SEC) has a strict stance on DeFi, while the Commodity Futures Trading Commission (CFTC) is more open to innovation. This lack of coordination could result in a mix of regulations that hinder DeFi’s growth.
1. Enforcement Risk: Regulators cracking down on DeFi, as seen in the SEC’s 2020 action against Compound, may lead to shutdowns and hefty fines, deterring participation.
2. Compliance Challenges: Clear regulations won’t eliminate complexities in determining responsibility, such as preventing money laundering, posing challenges for DeFi protocols.
3. Innovation Impact: Regulatory measures, like proposed bans on leverage use, may stifle DeFi protocols at the forefront of financial technology, limiting their ability to offer high-yield products.
4. Uncertain Future: The evolving regulatory landscape for DeFi makes predicting the future challenging, with real risks, as demonstrated by past enforcement actions, impacting the ecosystem.
Importance of Smart Contract Security
Let’s delve into why smart contract security is paramount and how to safeguard your ventures in the ever-evolving blockchain landscape.
Here are some consequences of insecure smart contracts:
Financial Losses: The DAO hack of 2016 stands as a stark reminder. Hackers exploited a vulnerability to drain millions from the project’s smart contract, sending shockwaves through the nascent DeFi space.
Reputational Damage: The Poly Network hack in August 2021, one of DeFi’s biggest, involved hackers exploiting a flaw to steal over $600 million in cryptocurrencies. Despite most funds being returned, the breach significantly damaged Poly Network’s reputation, raising concerns about DeFi security and eroding user and investor trust in the ecosystem.
Data Breaches: The 2018 Bancor Network breach, where hackers exploited a smart contract flaw to steal $12.5 million in Ethereum and $1 million in tokens, highlighted how such vulnerabilities can risk security breaches, potentially exposing sensitive user information.
Best Practices for Smart Contract Security
Smart contracts offer immense potential for automating trustless interactions. However, their immutability makes security paramount. A single vulnerability can lead to irreversible financial losses and erode trust in the entire ecosystem. This necessitates meticulous attention to secure coding practices and methodologies.
Language Specific Guidelines: Use established secure coding practices for the smart contract language you’re employing, such as Solidity’s best practices guide. These address common vulnerabilities like reentrancy attacks and integer overflows.
Access Control: Implement robust access control mechanisms to restrict functions and variables based on predefined roles and permissions. Avoid granting unnecessary privileges to prevent unauthorized manipulations.
Input Validation: Thoroughly validate all user inputs before processing them. Sanitize data to remove malicious code and ensure it conforms to expected formats and ranges.
Exception Handling: Gracefully handle unexpected conditions and errors using dedicated mechanisms like require statements. Avoid reverting transactions from within loops to prevent denial-of-service attacks.
Upgradability: Consider using proxy contracts or other mechanisms to fix bugs and add features after deployment, minimizing the risk of permanent damage from vulnerabilities.
Formal verification and automated security tools are pivotal in ensuring the integrity and security of blockchain-based applications, particularly through the rigorous analysis of smart contracts. QuillAI stands out in this landscape by offering AI-powered smart contract audits, providing developers with a robust platform for detecting and rectifying vulnerabilities in their Solidity-based contracts.
Collaborating with trusted smart contract auditing firms like QuillAudits for smart contract audits offers key advantages for DeFi and Web3 projects. It ensures expert vulnerability assessment and mitigation, enhancing trust with users and investors. QuillAudits, with its focus on DeFi Safety Audits, provides essential services for securing smart contracts in the evolving Web3 landscape.
Conclusion
In the DeFi world, it’s important to focus on the safety of smart contracts. Reducing smart contract risks can be done by checking smart contracts carefully, using reliable security tools, and following good safety habits. It’s also vital to remember that smart contracts, though innovative, can have security weaknesses. To stay safe and ahead in this area, it’s good to learn from resources and groups that focus on smart contract safety, risk management in DeFi, and staying up-to-date with rules. This not only makes individual projects safer but also makes the whole DeFi space more secure.
FAQs
- Who are Validators?
Validators in blockchain are nodes that verify transactions and propose new blocks to be added to the blockchain, ensuring consensus and security in the network.
- What is a mempool?
The mempool is a temporary storage area in a blockchain where pending transactions wait to be confirmed by miners and added to the next block.
- What are flash loans?
Flash loans are quick, unsecured cryptocurrency loans that must be borrowed and repaid within a single transaction block.
- What is SEC?
SEC stands for the U.S. Securities and Exchange Commission. It’s a regulatory agency overseeing securities and financial markets to protect investors and maintain fair, transparent, and efficient markets.
- What is CTFC?
CTFC refers to the U.S. Commodity Futures Trading Commission, a regulatory agency overseeing commodity and futures markets to ensure their integrity and protect market participants from fraud and manipulation.






















