Decoding the Radiant Capital Heist: A Comprehensive Analysis of the $4.5 Million Cyberattack
Summary
On January 3, 2024, Radiant Capital, a cross-chain lending protocol on Arbitrum, was exploited for approximately $4.5 million worth of ETH. The hack primarily resulted from vulnerabilities in the smart contract code and leveraged existing rounding issues in the codebase.
About Project:
Radiant Capital (RDNT) is a decentralized finance (DeFi) project that aims to consolidate fragmented liquidity across multiple lending protocols and chains. For more information, check out their website.
Vulnerability Analysis & Impact:
On-Chain Details:
Attacker Address :- 0x826d5f4d8084980366f975e10db6c4cf1f9dde6d
Attack Contract:- 0x39519c027b503f40867548Fb0c890b11728faA8F
Vulnerable Contract:- 0xF4B1486DD74D07706052A33d31d7c0AAFD0659E1
Attack Transaction:-0x1ce7e9a9e3b6dd3293c9067221ac3260858ce119ecb7ca860eac28b2474c7c9b
The Root Cause :-
The root cause of the incident with the Radiant Capital project was a flaw in the way they calculated token quantities. This calculation involved two main elements: precision expansion and rounding. Here’s a simplified explanation of both the root cause and how the vulnerability was exploited:
- Precision Expansion and Rounding in Calculation: The calculation method used by Radiant Capital involved expanding the precision of numbers (making them more precise) and then rounding them. They used a formula that can be summarized as (a * RAY + b/2) / b, where RAY is a large number (10²⁷) used to expand precision.
- Exploitation of the Formula: The attacker took advantage of this formula. The vulnerability lay in the handling of the variables ‘a’ and ‘b’. The key here is the relationship between the size of ‘a’ and ‘b’. When ‘b’ is significantly smaller than ‘a’, the rounding error is tiny and negligible. However, when ‘b’ is similar in size to ‘a’, the error becomes substantial.
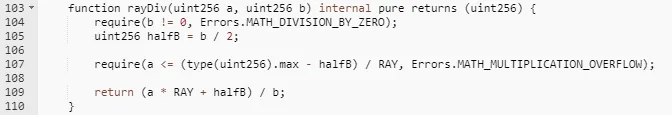


3. Manipulation of Values by Attacker: In the attack, the culprit manipulated the value of ‘b’ to be close to ‘a’. This caused a significant rounding error. For instance, if b = 3 and a * RAY = 10000, the computed result is 3333, which is 1/10000 less than the true value. In the case of a * RAY = 10000 and b = 3000, the computed result is 3, which is 1/10 of the true value. The computation in this instance equals 3/2.0001 = 1, as a result of the attacker manipulating the value of b to have a similar magnitude to a. There is a 1/3 difference between the calculated and actual values.
4. Impact of the Attack: By deliberately setting ‘a’ and ‘b’ to be close in magnitude, the attacker made the system round off numbers in a way that was significantly different from their actual value. This allowed the attacker to artificially expand profit margins.
Attack Process
- To begin the attack, the attacker first obtained a 3 million USDC flash loan through AAVE.
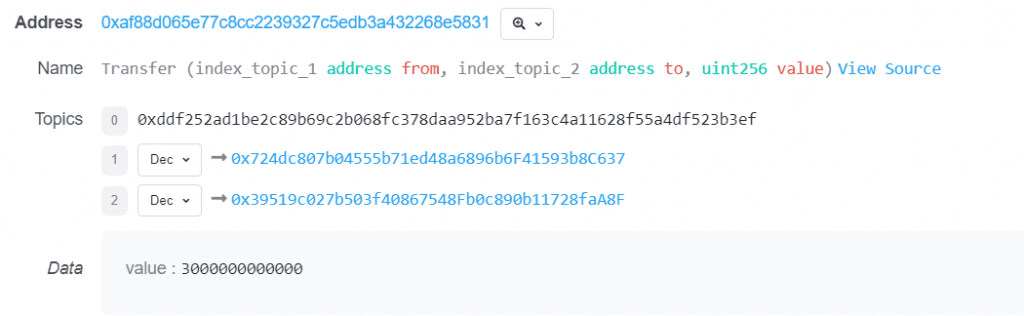


2. The attacker received two million rUSDCn token certificates in exchange for the pledge of two million USDC to the Radiant contract.
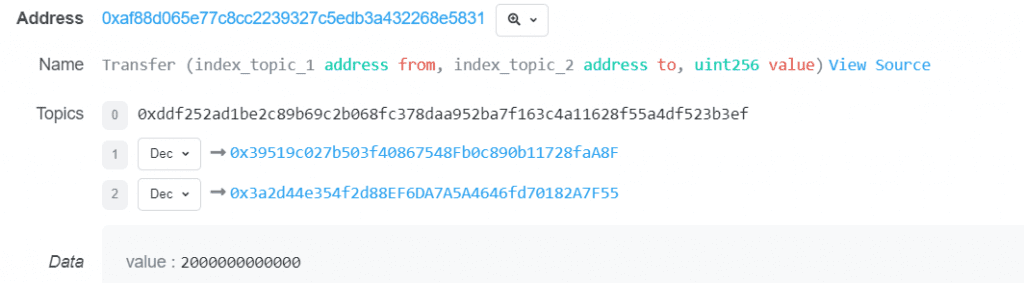


3. The attacker borrowed two million USDC using a flash loan obtained through the Radiant contract. In the callback function, the pledged USDC from the second step was extracted concurrently with the repayment of $2 million USDC. The attacker’s USDC was transferred into the contract by the flash loan function, which is also known as the transferfrom function. A 9/10000 fee was collected as liquidity for the pool.
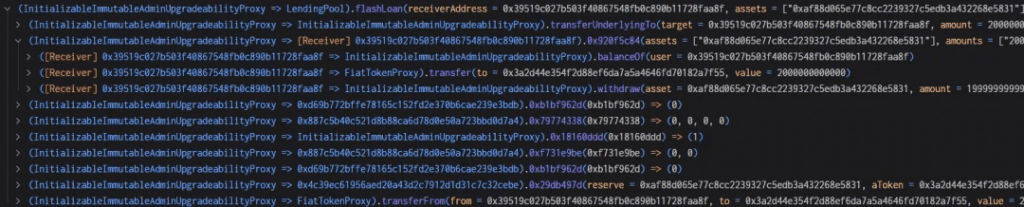


4. The outcome of this transaction was a manipulated liquidity index set at *271800000000.999999999999998631966035920 1e27. This value significantly surpassed the initial 1e27 observed before the manipulative actions occurred.
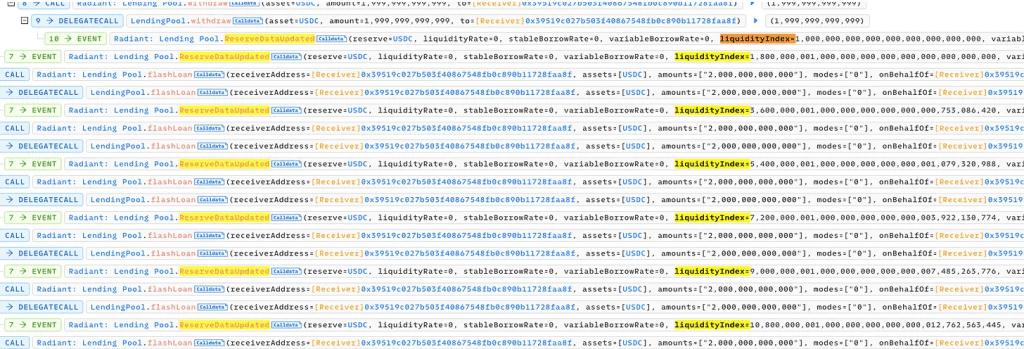


5. The attacker then made a fresh contract and funded it with 543,600 USDC. Rounding control is made easier by the fact that this amount is equivalent to twice the liquidityIndex value from step 4. The attacker pledged all 543,600 USDC into the Radiant contract, obtaining an equivalent amount of rUSDCn.
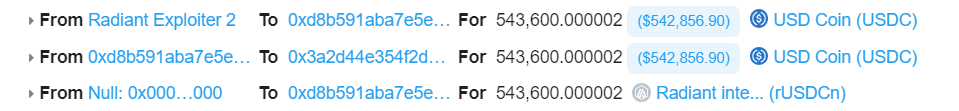


6. The assailant took out 407,700 USDC. As previously stated, 407,700 rUSDCn should have been burned; however, the burn function required exact expansion and rounding computations. The result is 1/3 less than the actual value, 40770000000000000000000000000000000/271800000000999999999999998631966035920 = 1.49999999, but rounding produces a 1. The attacker was able to withdraw 407,700 USDC because, as can be seen below, only 271,800 was burned as opposed to 407,700.
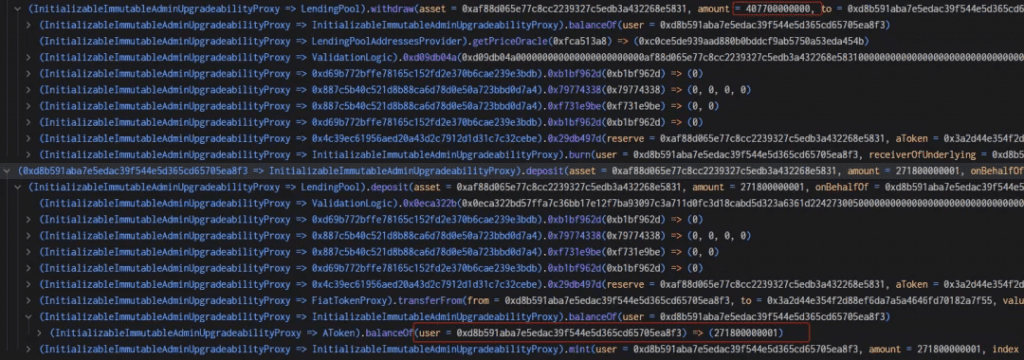


7 . The attacker then returns 271 800 USDC (+ 1 wei) to the account. The rayDiv now equals one wei rather than zero due to the additional wei. By depositing 271 800 USDC, the attacker gains back 1 wei of the USDC aToken and is able to repeat the withdraw and re-deposit cycle. For a total of about 2.8 million USDC, the attacker must retrieve the 2 million USDC that was transferred into the contract in step one, the 271k in flash loan fees, and the 543k that was deposited at the beginning of step three. At a rate of 135 900 USDC (407k — 271k) per iteration, the recovery occurs. There are 18 iterations netting 2 446 200 USDC and a final withdraw of 369 200 USDC for a total of 2 815 400 USDC, so close to 2.8 million which was the initial ballpark.
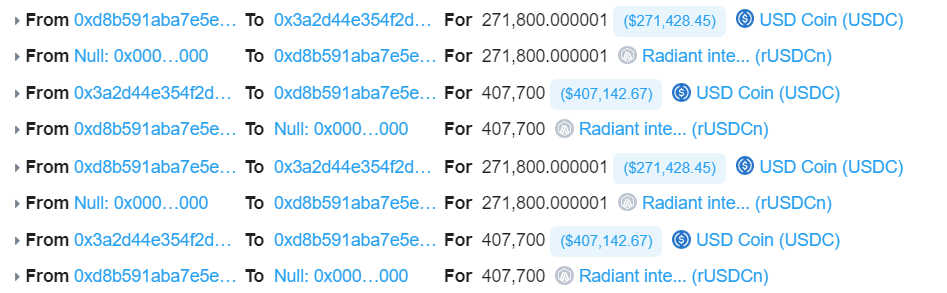


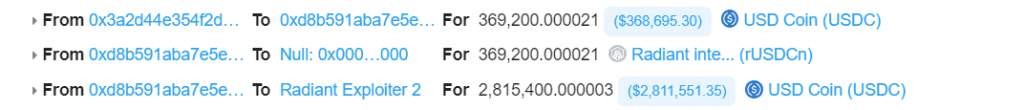


8. The hacker fled with the stolen ninety-plus WETH, recovered all of the USDC that was deposited, and paid back the AAVE flash loaHacks are repeated in two following transactions (here and here) with larger amounts (906 WETH extraction each) for a total of over 1900 WETH stolen.
After the Exploit➖
Following the exploit, the Radiant Capital acknowledged the hack via their Twitter decided to temporarily suspend lending and borrowing markets on the platform as a precautionary measure.
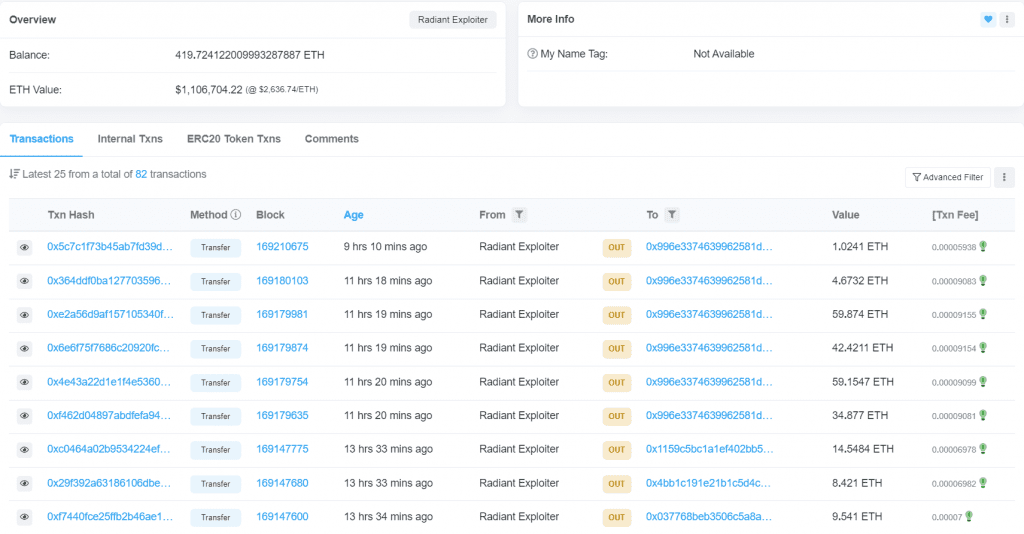
Funds Tracking ➖Following the security breach, the 1902 ETH that was stolen stayed in the hacker’s address without any activity. As of now, the current balance is 419 ETH, as the hacker is gradually moving the funds.


Timeline
- Jan 02, 18:53:23: The pool initialization occurs with insufficient data.
- Jan 02, 18:53:38: The attacker executes a flash loan, manipulating the liquidity index.
- Jan 02, 18:53:46 to 18:53:49: The attacker exploits a rounding error, withdrawing from the pool.
- Jan 3, 2024, 00:14 AM UTC: The Radiant Capital team receives notification of the exploit from the attacker. They promptly paused the protocol and initiated an investigation.
Today, we received a report of an issue with the newly created native USDC market on Arbitrum. After validation by Radiant developers and the wider Web 3 security community, the Radiant DAO Council paused lending/borrowing markets on Arbitrum temporarily while this is…
— Radiant Capital (@RDNTCapital) January 3, 2024
- Jan 3, 2024, 08:05 PM UTC: The Radiant Capital team identified the root cause of the exploit.
Radiant Capital was subject to a flash-loan-based exploit upon launching the new native USDC market on Arbitrum on January 2nd at 06:53:29 PM +UTC, leading to the protocol accruing bad debt in the WETH market totaling about 1.3% of total protocol TVL. 🧵1/10👇
— Radiant Capital (@RDNTCapital) January 3, 2024
- Jan 4, 2024: The pool paused as the Radiant Capital team continued to address the exploit and assess necessary remedial actions.


The Urgency of Web3 Security in the Current Scenario
As 2024 begins, we have witnessed four high-value theft cases. (Explore QuillMonitor, the web3 hacks & vulnerability tool, and analyze real attacks from 2020 onwards.) This series of events serves as a reminder that in the Web3 ecosystem, security precautions remain crucial! To prevent such vulnerabilities, the best Smart Contract auditors must examine the Smart Contracts for logical issues. QuillAudits stands at the forefront of this domain, offering top-notch cybersecurity solutions that safeguard millions in assets. Our team of experts is adept at utilizing advanced tools and techniques to ensure the highest level of security for your Web3 projects.
Partner with QuillAudits :
Interested in collaborating with QuillAudits? Explore our partnership opportunities designed to enhance Web3 security across the ecosystem:
- Affiliate program ( Refer and secure web3 )
- QuillAudits Partnership Programme ( Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products )
- Join Ambassador program






















