The combined financial damages stemming from Web3 breaches, phishing scams, and rug pulls escalated to a significant sum of $650M in H1 2023. Among them were hacks that caused an overall loss of roughly $471M, phishing scams contributing to a total loss of $108M, and rug pulls resulting in an approximate $75.87M loss.
Hack types include contract vulnerabilities, private key compromises, price manipulation, arbitrage attack, etc. Contract vulnerability exploits were the most common and financially detrimental attack, contributing to 56% of the overall losses.
This underscores a glaring truth: the vulnerability of smart contracts that underpin the DeFi ecosystem.
While some instances of hacks are due to inadequate security measures and phishing attempts, it is increasingly evident that the crux of the issue lies in the inherent weaknesses of smart contracts. These bugs, arising from coding errors, external price manipulations, or other factors, invariably result in the loss of millions of dollars.
In light of such circumstances, there is a dire need for smart contract vulnerability assessment. That brings us to this comprehensive guide which aims to delve into the salient aspects of smart contract auditing in fortifying the foundations of Blockchain and DeFi.
Why Is It Crucial To Ascertain Smart Contract Vulnerabilities?
1. Financial Assets at Stake: Smart contracts predominantly involve handling financial assets, making any vulnerability a potential threat to the monetary holdings of the protocol.
2. Immutable Nature: Once published, smart contracts become immutable due to the nature of blockchain technology, leaving no room for rectifying errors after deployment.
3. Irreversible Transactions: The changes induced in the blockchain’s state through flawed or deceitful contracts cannot be reversed, posing severe consequences.
So now the Data Speaks,
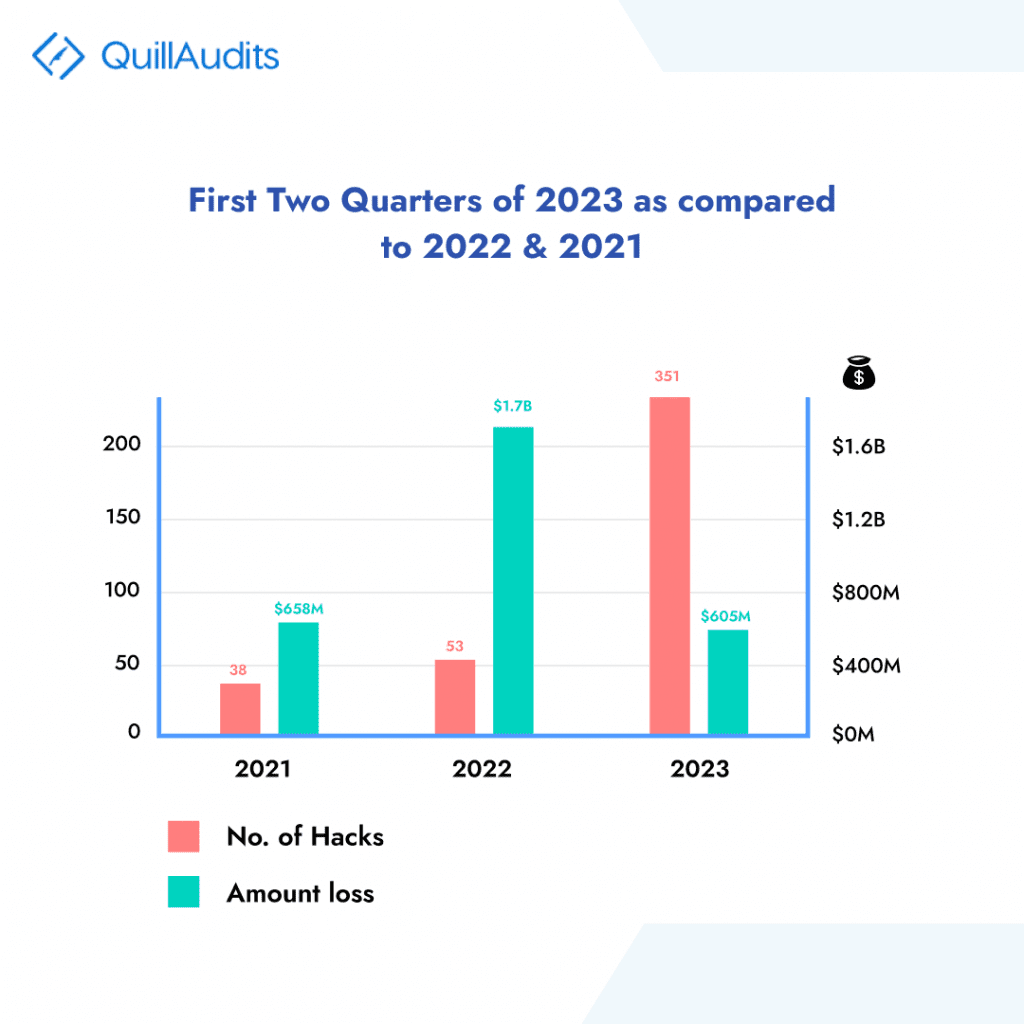


The graph above illustrates the losses incurred over the years. Although the overall loss resulting from hacks in 2023 has notably decreased compared to preceding years, the attack type that caused the most financial damage in 2023 remains to be smart contract vulnerabilities.
That brings us to know the common bugs that contribute to extensive exploits.
The Most Prominent Smart Contract Bugs to Watch Out For
Indirect Execution of Unknown Code
The fallback function in smart contracts allows for indirect execution, leading to discrepancies. There are various scenarios where the fallback function can be mistakenly called, making it essential to handle such cases diligently. Such scenarios include,
- Calling a function of another contract using ABI: Typos or incorrect signatures can trigger the fallback function.
- Deposit to another contract: Initiating a deposit can inadvertently invoke the fallback function.
- Calling a function using the API: Mistakes in declaring the interface can lead to the execution of the fallback function.
Reentrancy
Reentrancy is a common vulnerability in Ethereum smart contracts where attackers can exploit vulnerable contracts and steal funds by re-entering the contract before its state is updated. It is a much common practice to use the fallback function for re-entry.
Incorrect Calculation of the Output Token Amount
Smart contracts dealing with significant token amounts are susceptible to errors in fee calculations and token transfers, leading to financial losses for users. It includes mishandling decimals, incorrect order of operations leading to fee calculation errors, forgotten accuracy constants, etc.
Interface/Naming Issues
Issues with contract interfaces and naming can create vulnerabilities, enabling anyone to exploit and become the contract owner that allows them to access accumulated funds.
Time Component
Smart contracts with time-dependent logic are at the brim to miner manipulation of timestamps, providing hackers with advantages over other contract parties.
Incorrectly Handled Exceptions
Solidity exceptions can lead to vulnerabilities if not handled properly, leaving contracts open to attacks from malicious users.
Incorrect Work with ERC20 Token
Custom implementations of ERC-20 tokens can lead to discrepancies and non-functional contracts, blocking funds and causing disruptions.
Knowing all these presses the need for smart contract auditing to rectify these errors before the deployment of contracts to prevent any major loss.
How Instilling Smart Contract Security through Professional Auditing Helps?
Implementing smart contract auditing practices facilitates the early detection and resolution of issues before contract deployment. Conducting audits during the development phase allows potential vulnerabilities to be identified and rectified proactively, mitigating risks to the project. This approach minimizes costs and efforts associated with addressing issues in later stages while simultaneously mitigating the impact on users and stakeholders.
Enhanced Code Quality
The core of auditing practices is the focus on code review and analysis, leading to an overall improvement in the quality of the smart contract’s codebase. Auditors offer valuable insights and recommendations for code optimization, adherence to best practices, and improved readability. Consequently, this results in a more maintainable and efficient code, significantly reducing the likelihood of future bugs.
Ensuring Compliance and Regulation
Incorporating smart contract auditing practices guarantees adherence to legal and regulatory requirements. Meticulous auditing verifies the contract’s compliance with relevant laws, industry standards, and governance frameworks. This becomes particularly crucial for projects operating in regulated sectors, such as healthcare or finance, where compliance is of utmost importance.
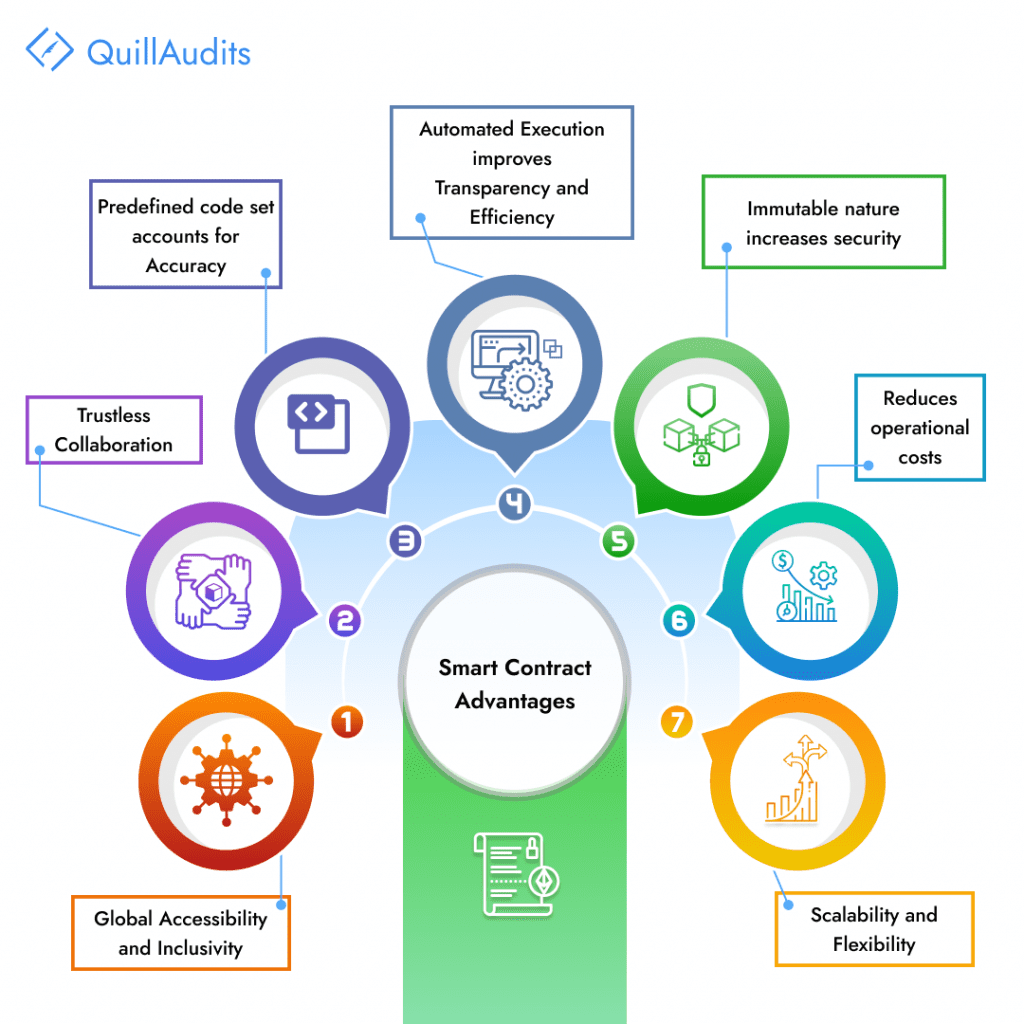


The Methodical Approach of Conducting Code Audits By Security Firms
Defining Audit Scope
The security firm precisely defines the scope of the audit. This involves determining the specific branch and contracts that will undergo scrutiny, as well as noting down their respective commit hash. Determining the audit scope sets the foundation for a targeted and thorough analysis.
Requirement Gathering
Before delving into the code, comprehensive data gathering happens. This includes collecting essential information about the smart contract’s functions, their input parameters, expected outputs, and the underlying business logic supporting these functions. The identification of critical modules from a business perspective holds significant importance in performing audits.
Manual Analysis
A hands-on approach is adopted to understand the code completely from start to end. Security experts employ various attack scenarios and attempt to exploit potential vulnerabilities. They check for possible attack vectors and assess architectural loopholes. Thereby, this phase emphasizes best security practices and gas optimization techniques.
Functional Testing
To ensure the robustness of the smart contract, thorough functional testing is carried out. The security firm creates detailed test cases to examine the behaviour of functions under various edge cases and scenarios. This testing helps reveal any hidden flaws in the code logic.
Formal Verification of Smart Contract
The security firm employs automated mathematical proofs to verify that the smart contract‘s source code adheres to specified formal specifications. This step provides a higher level of confidence in the correctness of the contract’s implementation.
Symbolic Execution
Symbolic execution is utilized to explore all possible execution paths of the smart contract without actually executing it. By treating variables as symbolic values rather than concrete ones, security experts analyze complex interactions and potential vulnerabilities in the code.
Fuzzing
The fuzzing technique subjects the smart contract to a barrage of invalid, unexpected, and semi-random data inputs. This process aims to simulate real-world conditions and interactions to identify and address unexpected behaviors and vulnerabilities.
Invariant Testing
Invariant testing involves making random function calls with various data inputs to identify potential invariants that must always hold true. By attempting to break these invariants, security experts uncover hidden weaknesses.
Automated Testing
The security firm utilizes specialized tools like Slither and MythX for automated testing to streamline the audit process. These tools can efficiently scan the codebase for common vulnerabilities and potential issues.
Audit Report Submission
The culmination of the code audit results is given in a comprehensive report. It lists down all identified issues, providing detailed descriptions, code snippets, severity assessments, proof of concept examples, and recommended mitigation steps. This report serves as a valuable resource for developers to address the identified vulnerabilities effectively.
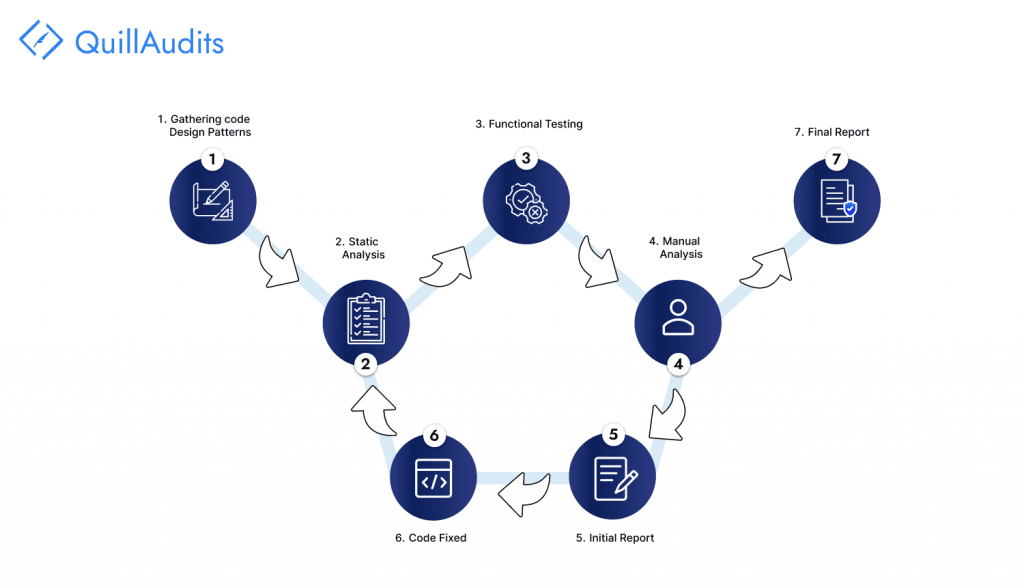


Some Noteworthy Smart Contract Audit Tools
1. Oyente: Oyente examines the contract’s code to identify common vulnerabilities like reentrancy, timestamp dependence, and other potential issues that could lead to vulnerabilities.
2. Mythril: Mythril uses symbolic execution to identify potential security vulnerabilities in smart contracts.
3. Sereum: Sereum is a framework designed to enhance the security analysis of Ethereum smart contracts by emulating the Ethereum Virtual Machine (EVM) code.
4. ContractFuzzer: ContractFuzzer is a security analysis tool that uses fuzzing techniques to discover bugs and weaknesses that traditional analysis might miss.
5. ILF (Intermediate Language Fuzzer): ILF is a tool that performs security analysis on the intermediate language (IL) code used in Ethereum smart contracts, helping to identify potential vulnerabilities.
6. Slither: Slither is an open-source static analysis framework that helps developers and auditors identify security issues and bad coding practices in their contracts.
7. RecChecker: RecChecker is a tool for detecting vulnerabilities related to recursive calls in Ethereum smart contracts.
Key Factors Involved in Estimation of Project Audit Cost
The complexity of the Project: Complex contracts with intricate logic or extensive external interactions demand more time and effort during the review process, leading to higher audit expenses. The size of the smart contract’s codebase, measured by the number of lines of code, can also significantly impact the overall smart contract auditing cost.
Distinctiveness of Blockchain Platform: Variations in unique features and architectures of different platforms, like Tron, Solana, and Polkadot, can influence the overall audit expenses. Factors like Ethereum’s gas fees, storage fees, and contract execution processes also play a key role in determining cost estimation.
The expertise of Auditing Firm: Highly regarded auditing firms or individuals with a reputation, experience and proven track record of successful audits might charge a premium for their services. Additionally, the tools, technologies, and post-delivery services required for the audit, as well as the intricacies of project management, impact the cost.
QuillAudits is a preeminent web3 security firm with an exemplary track record of successfully auditing over 850 projects and safeguarding over 30 billion in assets. For those seeking an ideal smart contract auditing firm, QuillAudits may be the destination of choice. Our core principles revolve around open communication and transparency, empowering clients with the ability to obtain a cost estimate for their projects using our pricing calculator. By simply providing the necessary inputs about the project, the calculator promptly generates a price estimate.
FAQs
Do smart contracts need to be audited?
While blockchain technology offers inherent security, smart contracts may still have issues like coding flaws, errors, or vulnerabilities. Therefore, conducting a smart contract audit is essential to address and rectify any potential flaws before they are deployed on the blockchain and put into use.
How much it costs for smart contract audits?
The costs for smart contract audits may vary significantly depending on the code’s intricacy and the project’s complexity in specific situations. To provide an approximate estimate of the auditing cost, QuillAudits presents a dedicated pricing calculator. By inputting the details of your project, you can have the estimate of the audit cost in hand readily.
How to learn smart contract Audits?
Quillacademy is a comprehensive learning platform for individuals seeking to delve into web3 security. From a wide array of course offerings to conducting workshops, Quillacademy provides all the necessary resources to become proficient in smart contract auditing.
What is the main role of smart contract auditors?
Smart contract auditors study the technical docs of the project, review and test the code to identify vulnerabilities and ensure the contract functions as intended. They communicate their findings effectively to developers, project managers, and other stakeholders, providing recommendations on sorting it out for the project to go hack-free.
How do I avail the smart contract auditing service for my Web3 protocol?
We have our experts at a click away! Visit our website to live chat or reach out via LinkedIn, Twitter or Telegram.






















