Blockchain technology, with its decentralized nature, has revolutionized the way we approach transparency and efficiency. This technology delegates tasks to multiple validators within the network, ensuring a more secure and reliable system.
Validators can either be selected members or open to anyone, leading to two types of blockchain networks: permissioned and permissionless.
Based on the choice of validator network, we have two classifications:
- Permissioned blockchains- restricted to people with access
- Permissionless blockchains- open to public
As blockchain technology continues to gain traction, industry experts from finance, supply chain, and IoT are increasingly turning to Hyperledger for their operations. Hyperledger is a permissioned blockchain, meaning the identities of its network members are validated.
This feature, along with its portability, makes Hyperledger a top choice for business applications. But before we delve into the security aspects of Hyperledger, let’s first understand its overall structure and functionality.
Hyperledger: An Introduction
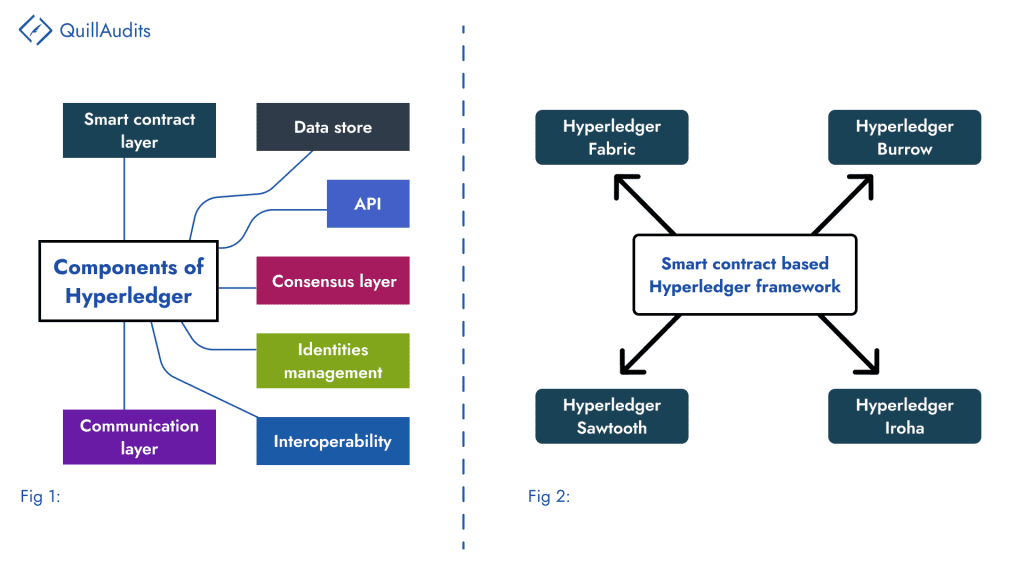
Established in 2015, Hyperledger provides a platform for businesses to develop blockchain applications with its user-friendly and interoperable features. It offers five distinct frameworks: Sawtooth, Fabric, Burrow, Iroha, and Indy, each designed to cater to diverse use cases.
Hyperledger’s open-source, permissioned nature makes it suitable for a wide range of industrial applications. Its scalability, performance, and high level of trust, along with data access rights specific to network members, make it a preferred choice for businesses.
Moreover, Hyperledger offers flexibility in choosing a programming language such as Java or Go for building smart contracts, providing control over peer nodes and ensuring high scalability with minimal performance losses.
Hyperledger Fabric and Hyperledger Besu: The Preferential Choice in the Business Environment
Technologies such as Fabric and Besu that come within the Hyperledger umbrella are widely used for many corporate projects. Before long, let’s find what’s so interesting about them that captivates the market attention.
Hyperledger Fabric
It works on an open, enterprise-standard DLT(distributed ledger technology) and comes with advanced privacy controls. It lets only the desired data to be shared within the “permissioned” set of participants.
It follows permission voting-based consensus with a central authority passing orders. Widely adopted in business environments to instil a decentralized trust among the network of known employees/participants.
Another noteworthy attribute is its modular structure. The modular design of the Hyperledger Fabric allows the use of different algorithms for different purposes, such as an algorithm for encryption, another for identity and for consensus and so on.
And to top it all, it comes with a pluggable architecture that can be tailored according to the industry’s needs.
We can clearly see all the reasons why corporates are fond of Hyperledger Fabric.
Hyperledger Besu
Launched in 2019, Besu is an Ethereum-based technology that enables enterprises to develop applications on both public and private networks. The hybrid approach has gained rapid adoption for Besu technology.
Regarding its technicalities, Hyperledger Besu facilitates being built on the Ethereum core network and also for creating private business networks. It is written using tools used by the Ethereum development community, such as Truffle, Remix, etc.
It permits the use of different consensus algorithms. Like, Proof of Authority can be used for private networks and Proof of Work for Public Ethereum networks. Moreover, it is EVM compatible, allowing the deployment and execution of smart contracts & Dapps on both public and private networks.
Besu is highly secure for performing transactions. Privacy capabilities, high performance, network access, and transparency are what make Hyperledger Besu a preferred choice for business.
Architectural Layout of Hyperledger
The architecture of Hyperledger is designed to provide a secure solution with a user-friendly programming interface. It consists of several layers, including identity verification, consensus, smart contract, communication, data storage, interoperability, and API.


Highlighting Hyperledger Security Threats
Concerning the Hyperledger blockchain, possible attacks can surface from the interconnected components such as smart contracts, consensus, chaincode and privacy preservation.
Let’s dig further deep into the security threats.
- Consensus Threats
Hyperledger consensus work on CTF(Crash Fault Tolerance) or BTF(Byzantine fault tolerance). Any threat or manipulation of the consensus can disrupt network security. However, installing a web application Firewall scans the incoming web traffic and mitigates risks at the consensus level.
In the permissioned blockchain, each peer in the network holds accountability for their behaviour, which rules out the possibility of malicious acts.
- Smart contract vulnerabilities
Coding flaws and design errors in smart contracts can be attributed to the blockchain’s faulty behaviour, followed by a series of attacks.
Some of the coding errors arise from Random key generation, Timestamp, State variables, Chaincode sandboxing, Double spending due to concurrency and so on.
- Network Security Concerns
Certain prominent risks challenge the network’s security, crashing the network’s operations. It includes,
- Compromised membership service provider (MSP): Since Hyperledger is a permissioned blockchain, it is centralized, with authorities that control it. And MSPs play a critical role in managing the identity registration of peers and clients in the network.
Therefore, a compromised MSP can cause great trouble in adding or removing identities. Thereby, the attacker manages the network nodes, which can lead to other errors such as double spending, identification attacks and so on.
- Endorser-related issues: Approving transactions by endorsers in the Hyperledger network would require their identity and signature. Suppose any difference in opinion between endorsers would lead to the creation of conflicts impacting network security.
Furthermore, it bestows the possibility of launching DoS and Wormhole attacks. Launching a DoS attack on selective endorsers to halt the approval of transactions by them. Similarly, Wormhole attacks on peers could cause leakage of private information of a particular channel.
Insights On Risk Mitigation Techniques
- DoS attacks can be prevented by monitoring network traffic through a firewall or intrusive detection methods.
- The hosting infrastructure must be kept resistant to MSP compromises to protect against MSP-related issues.
- Constant check over the security alignment of the P2P network
- Keeping all the related software updated to the recent versions
- Smart contract code needs to undergo security audits by professionals to ensure there are no discrepancies
This brings us to know about a trustworthy Web3 auditing firm to ensure that the security of your project is in place.
What Do We Do At QuillAudits To Ascertain The Project’s Security?
At QuillAudits, we provide comprehensive auditing services to ensure the security of your Hyperledger project. Any shortcomings in the code or project are thoroughly investigated to ensure the overall security of the Hyperledger.
The auditing service coverage includes,
- Hyperledger security code audit
- Vulnerability detection
- Bug fixes
With the increasing number of hacks leading to significant losses, the need for auditing services has never been more critical.
FAQs
What is the difference between Crash fault tolerance(CFT) and Byzantine fault tolerance(BFT)?
BFT is if a system can resist ⅓ of the nodes failing or acting maliciously. CFT is designed to offer resiliency to the protocol to withstand algorithm or any component failures in the system.
What is Hyperledger written in?
Many components in the Hyperledger are written using the Go programming language. Other languages, such as Java and Node.js, are also used.
Why is Hyperledger preferred amongst Enterprises?
It uses Transport layer security(TLS) for secure communication between the nodes, which is why it is preferred the most.
What is the need for a Hyperledger security audit?
External security audit and formal verification of the project look at the minute and overlooked details during the development, which, otherwise left unnoticed, would easily fall for hacks.






















