Introduction
Imagine a lively market where diverse people trade things and services, relying on trust and openness. The key challenge is to secure the integrity of transactions without relying on intermediaries.
This is where blockchain comes into play, serving as a cutting-edge database system that enables open sharing of information within a business network. The information is stored in connected blocks. Any changes to the chain require approval from the whole network to maintain order.
This method guarantees a safe and unchangeable record for tracking transactions, orders, and accounts. It has built-in measures to prevent unauthorized actions, ensuring a reliable and dependable transaction history.


Traditional databases face challenges in accurately recording financial transactions, especially in scenarios like property sales. People can track money exchanges, but trust issues can arise if either party disagrees with the transaction. To prevent legal complications, a reliable third party must oversee and authenticate transactions, introducing complexity and a single vulnerability point.
Blockchain addresses these concerns by establishing a decentralized, tamper-resistant transaction recording system. In a property sale, for instance, separate ledgers are created for the buyer and seller.
Transactions require approval from both parties and are instantly updated in their respective ledgers. Any tampering with historical transactions affects the entire ledger. These blockchain features have driven its adoption in various sectors, including the development of digital currencies like Bitcoin.
Bitcoin, launched in 2009, wasn’t just the first cryptocurrency; it also birthed the revolutionary technology behind it – the blockchain. This digital ledger has changed industries by securely recording information in a transparent and tamper-proof way.
Before Bitcoin, digital currencies struggled with the double-spending problem, where a single digital unit could be used multiple times. The Nakamoto Consensus, named after Bitcoin’s pseudonymous creator, introduced a set of rules to tackle this issue.
Central to these rules is the proof-of-work (PoW) algorithm, which requires participants to solve complex problems, making it costly and deterring malicious activities. This algorithm is employed within a Byzantine Fault Tolerant (BFT) peer-to-peer network, enhancing the network’s resilience against failures or attacks.
In a decentralized system like Bitcoin, multiple computers (miners) need to agree on the validity of transactions and the state of the blockchain. This is where the consensus mechanism comes in. Bitcoin’s PoW system requires miners to solve complex mathematical puzzles to earn the right to add a block to the blockchain. This computationally intensive process secures the network against malicious actors trying to manipulate transactions.
Understanding the Problem: The Byzantine Generals Problem
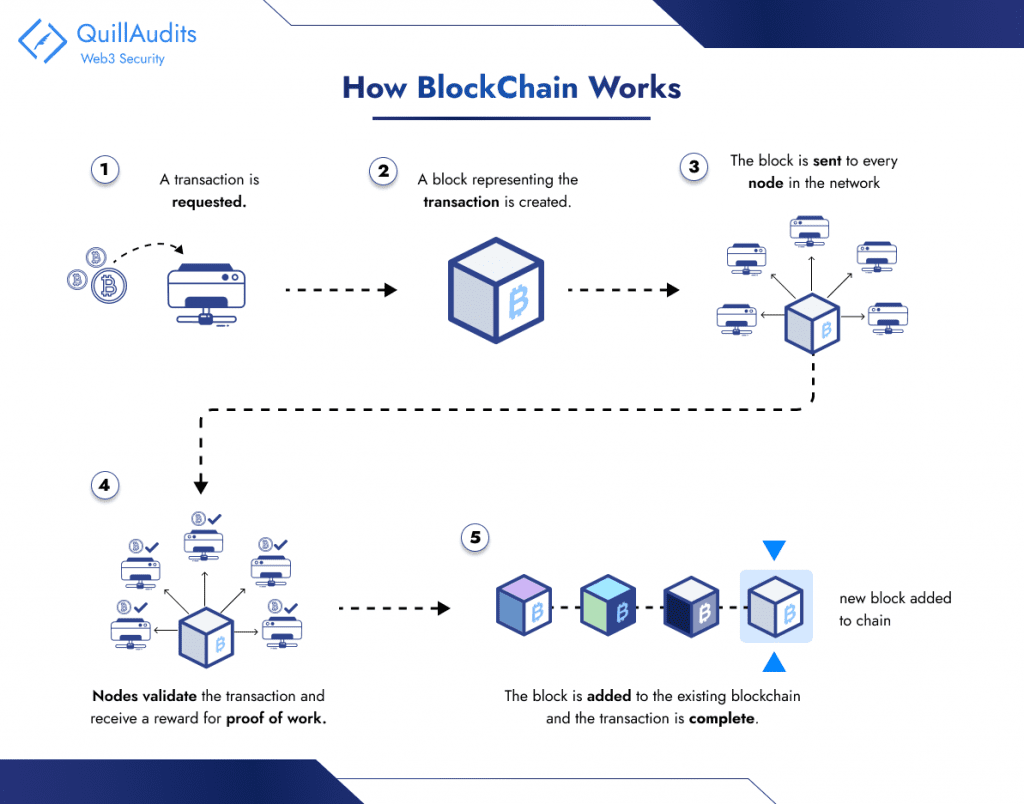
Imagine a battlefield surrounding the Byzantine Empire’s capital. Several Byzantine generals, each commanding their own army, must coordinate their attack on the city to succeed. Victory hinges on unanimous agreement: all generals must attack simultaneously, or the defenders will defeat them one by one.
However, there’s a twist:
Treacherous generals: Some generals might be traitors, working for the enemy or with their own agendas. They can send misleading messages or simply refuse to cooperate.
Unreliable communication: Messengers carrying orders can be intercepted, delayed, or even impersonated. The generals can’t be sure of the information they receive.


Challenges in a Trustless Environment
- Malicious Actors: Byzantine nodes can intentionally disrupt the network by Sending conflicting messages, Confusing other nodes, and hindering consensus.
- Denying service: Refusing to participate in the consensus process. Fabricating data: Creating false information to manipulate the network.
- Unreliable Communication: Technical issues can lead to Message delays, Transactions or blocks taking longer to propagate, potentially causing inconsistencies.
- Message loss: Information gets lost in transit, creating gaps in the network’s knowledge.
- Reaching Agreement: Even with honest nodes, achieving consensus efficiently can be difficult, especially with a large number of participants. Different consensus algorithms offer varying trade-offs between speed, security, and fault tolerance.
Nakamoto Consensus: A Solution to the Byzantine Generals Problems
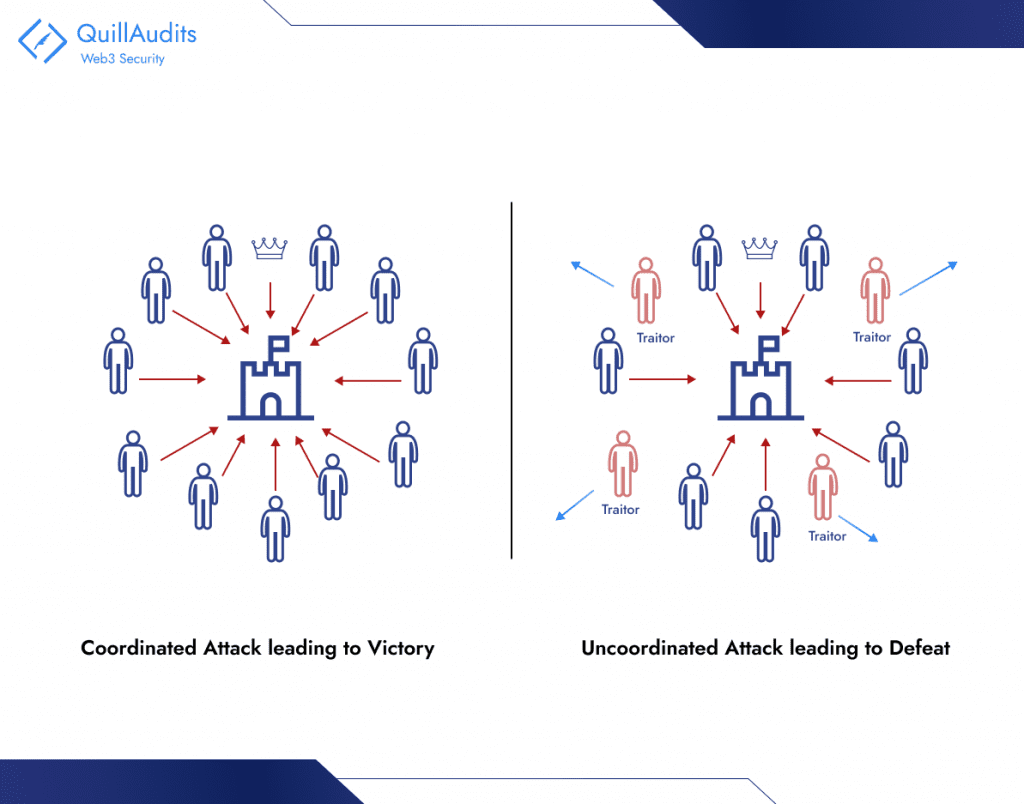
In the Byzantine Generals Problem, reaching a common decision, like in blockchain, is vital. This is similar to the Nakamoto consensus in blockchain, a key part of Bitcoin.
The blockchain acts as a public record, like a ledger, showing all Bitcoin transactions. This is crucial for Bitcoin consensus rules. When all Bitcoin network users, or nodes, agree on transaction details and their sequence, they confirm ownership and enable a trustworthy, decentralized money system, avoiding central control. This is what bitcoin consensus is about.
Blockchain’s decentralized nature depends greatly on consensus techniques, like the Nakamoto consensus on permissionless and nameless systems, to validate transactions. It’s a network where users can see everything transparently, fostering trust. Its shared ledger distinguishes it from other methods.
Understanding and analyzing Nakamoto consensus reveals its potential for any system requiring accurate verification. This describes the Nakamoto consensus based on permissionless and nameless principles, a cornerstone in blockchain technology.
1. Proof-of-Work (PoW): Solving Puzzles for Power
Imagine miners competing to solve complex mathematical puzzles. The first to find a solution gets to add a block to the blockchain, a publicly viewable ledger of transactions. But solving these puzzles takes real computational power and energy, acting as a “cost function” to discourage bad actors. Miners are incentivized to be honest, as fraudulent blocks face rejection by the network.
2. Blockchain and Hashing: Building a Chain of Trust
Think of the blockchain as a series of interlocking blocks. Each block contains data (transactions) and a unique cryptographic fingerprint called a hash. This hash is created by chaining together the previous block’s hash and the new data. Changing any data within a block invalidates its hash and all subsequent hashes, making tampering virtually impossible.
3. Longest Chain Rule: Might Makes Right (Almost)
Now, imagine multiple miners finding solutions and creating blocks simultaneously. The network adopts the longest chain principle, accepting the chain with the most accumulated PoW as the true version of the blockchain. This incentivizes miners to build upon the existing chain, rather than starting their own, solidifying consensus.
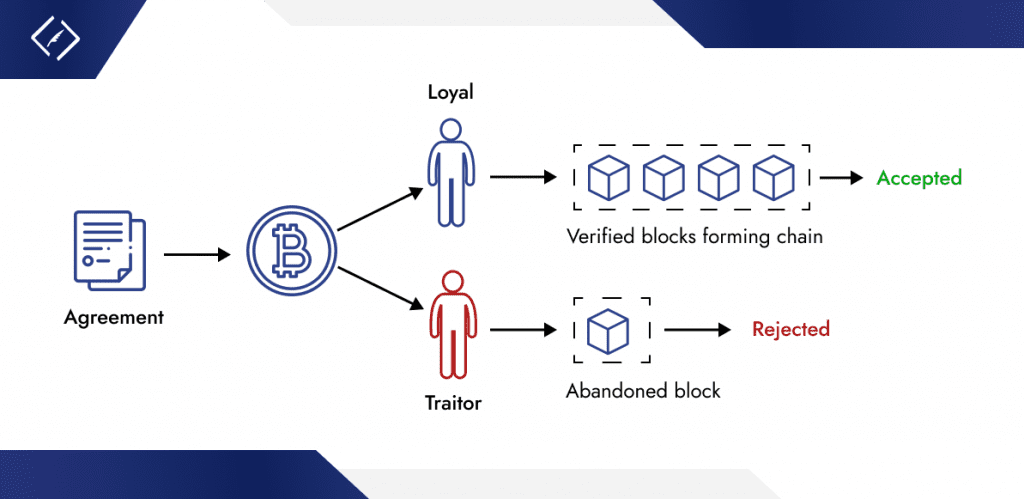


Illustration of Consensus and Prevention of Double-Spending:
- Miners compete to solve mathematical puzzles through PoW, ensuring that only valid blocks are added to the blockchain.
- Each block is securely linked to its predecessor via cryptographic hashing, making any alteration of past transactions easily detectable.
- The longest chain rule ensures that the blockchain version accepted by the majority is always considered the legitimate one.
This framework collectively secures the blockchain, facilitates consensus among participants, and effectively prevents double-spending. Double-spending is averted because once a transaction is confirmed in a block, altering it would require re-mining that block and all subsequent blocks at a faster rate than the rest of the network, which is practically infeasible due to the PoW mechanism.
Benefits of Nakamoto Consensus
Decentralization: The strength of blockchain is derived from Nakamoto Consensus, which distributes power among numerous nodes to fend off censorship and eliminate single points of failure. With just an internet connection needed for worldwide, unrestricted participation, this decentralized system promotes financial inclusion without regard to location.
Trustlessness: Blockchain technology reduces reliance on outside parties to validate transactions, allowing for an automated, self-governing system that gives users direct control over their data and assets, promoting autonomy and minimizing bias.
Security: Byzantine Fault Tolerance and Proof-of-Work, two strong cryptographic foundations built into the blockchain, guarantee tamper-proof records and system resilience against interruptions. Incentives based on game theory help miners better align their efforts with network security and stability.
Transparency: Blockchain ensures public, verifiable transactions and an immutable history, enhancing trust, accountability, and market efficiency through transparent, unalterable records.
Criticisms and Potential Alternatives
Nakamoto Consensus, the engine behind blockchains like Bitcoin, has changed finance and tech, yet it has flaws. Using Proof of Work (PoW), it demands huge energy, raising sustainability issues. PoW also limits scalability, causing slow transactions and high fees and hindering widespread adoption. Recognizing these problems is vital for advancing decentralized systems.
Fortunately, the blockchain ecosystem is brimming with innovation. To overcome the drawbacks of PoW, researchers and developers are exploring alternative consensus mechanisms, with Proof of Stake (PoS) gaining significant traction. In PoS, validators are chosen based on their stake in the network’s cryptocurrency, eliminating the need for energy-intensive mining. This not only reduces energy consumption but also potentially increases transaction speeds and scalability.
Conclusion
The Nakamoto Consensus is key to Bitcoin’s success. It’s a novel method that solves the Byzantine Generals Problem, ensuring secure and decentralized digital transactions. This is achieved by combining Byzantine Fault Tolerance with Proof-of-Work, creating a network that protects against fraud and maintains transaction integrity. However, there’s debate over its sustainability and energy use. This has led to exploring alternatives like Proof of Stake for more scalable blockchain solutions. It’s vital for everyone, from enthusiasts to skeptics, to understand and discuss these technologies. They are shaping the future of decentralized systems and can lead to a more efficient, inclusive world. The evolution of Bitcoin and blockchain is an unfolding story, open for all to contribute to.






















