Web3 has transformed our identities into vital components of online interactions, transactions, and connections. Unique Identifiers (UIDs) address privacy, security, and data control challenges, securing our digital footprints.
UIDs serve as the backbone of the Web3 framework, essential for identifying and managing users, assets, and transactions in a decentralized environment. But the uniqueness of UIDs also brings potential risks, making them a target for malicious actors. As we explore the world of UIDs in Web3, it’s crucial to understand the common vulnerabilities they face. Robust security measures are necessary for safe digital identities and a secure online environment.
Introduction to Unique Identifiers in Web3
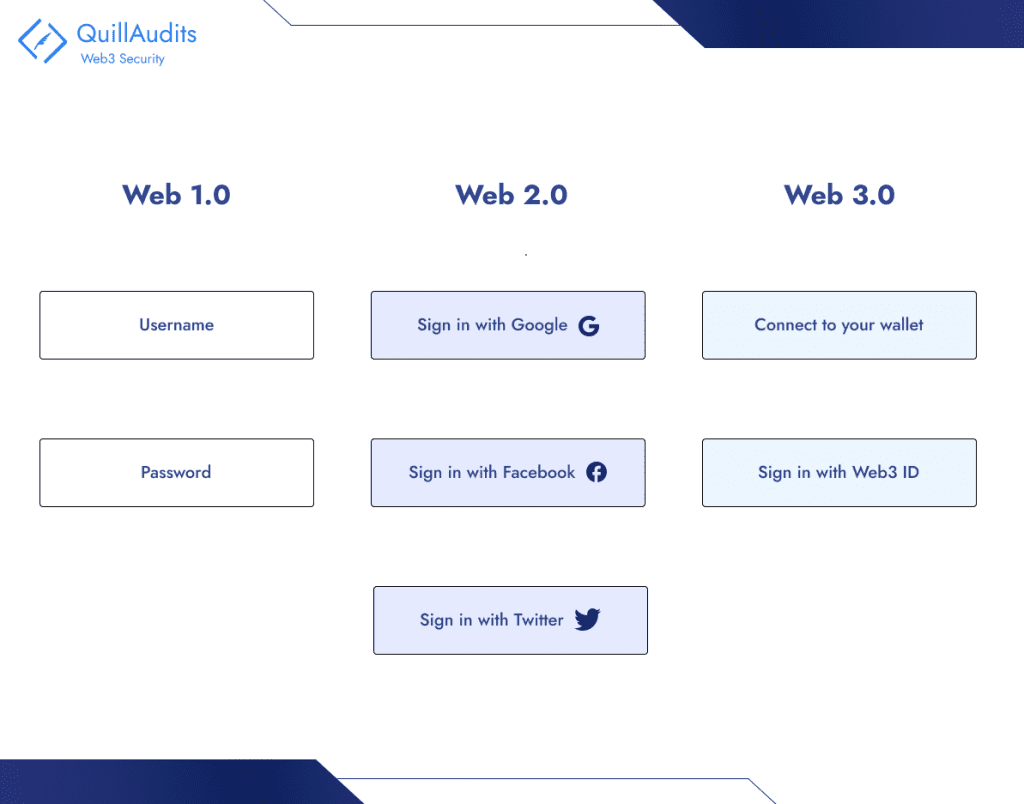


Unique Identifiers (UIDs) in Web3 serve as foundational components for distinguishing and tracking individual entities within decentralized digital ecosystems. These identifiers can take multiple forms, catering to different layers of interaction and functionality within the blockchain and decentralized application (dApp) landscapes.
On-chain addresses are one of the most common types of UIDs, representing specific wallet addresses on blockchain networks such as Ethereum. These addresses are public and provide a transparent means for executing and recording transactions.
Off-chain identifiers, on the other hand, offer a layer of pseudonymity, functioning as usernames or handles within dApps, allowing users to interact with decentralized platforms while maintaining a degree of privacy.
Token IDs represent another crucial form of UIDs, uniquely identifying each token within a given project, especially in contexts like Non-Fungible Tokens (NFTs) where uniqueness and provenance are key.
These diverse UIDs are integral to the functionality, security, and user experience in Web3, enabling seamless interaction, ownership verification, and asset tracking in a decentralized environment.
To better understand digital identity, it is useful to understand the aspects that make up our identity online. Digital identity is built on a foundation using various standards, frameworks, protocols and data models. The Web3 digital identity landscape can be categorized into four essential building blocks: identifiers, identity attributes, reputation and digital collectibles and assets – the combination of which form an individual’s unique digital identity.
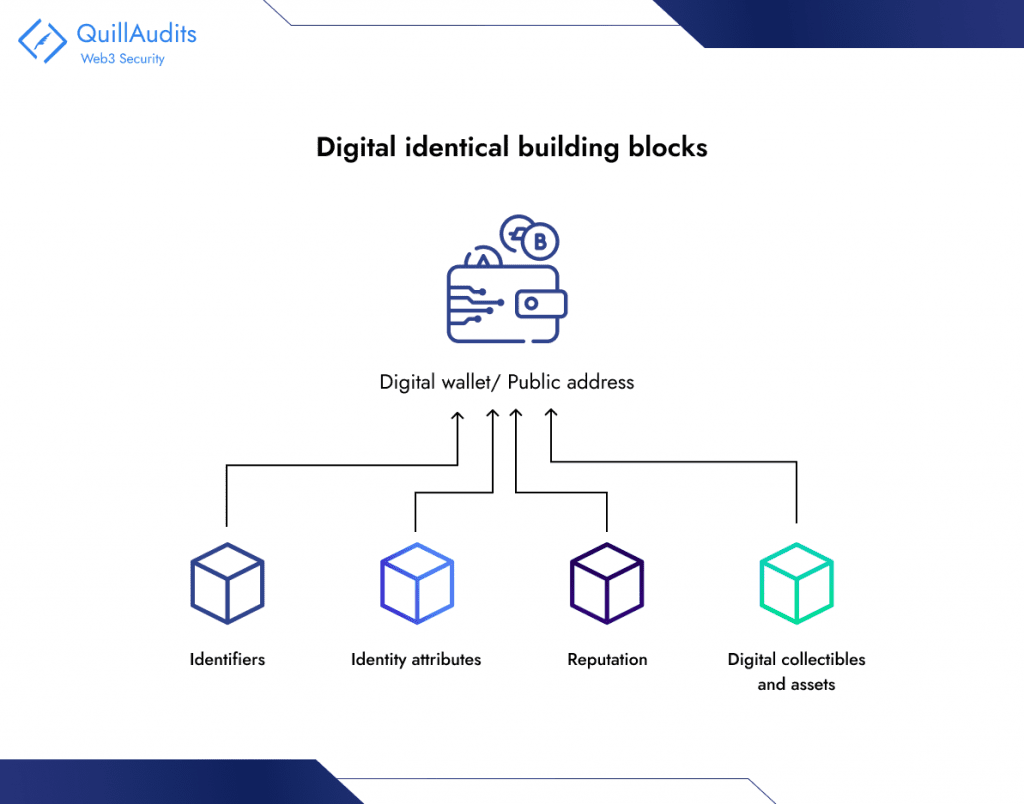


Identifiers
Identifiers are ‘tags’ that we use every day. Names, email addresses, account numbers, social handles are all forms of identifiers. In the context of blockchains, a person’s ‘public’ blockchain address is their primary identifier for any blockchain-based interaction, and is typically a unique string of alphanumeric text.
Web3 identifiers
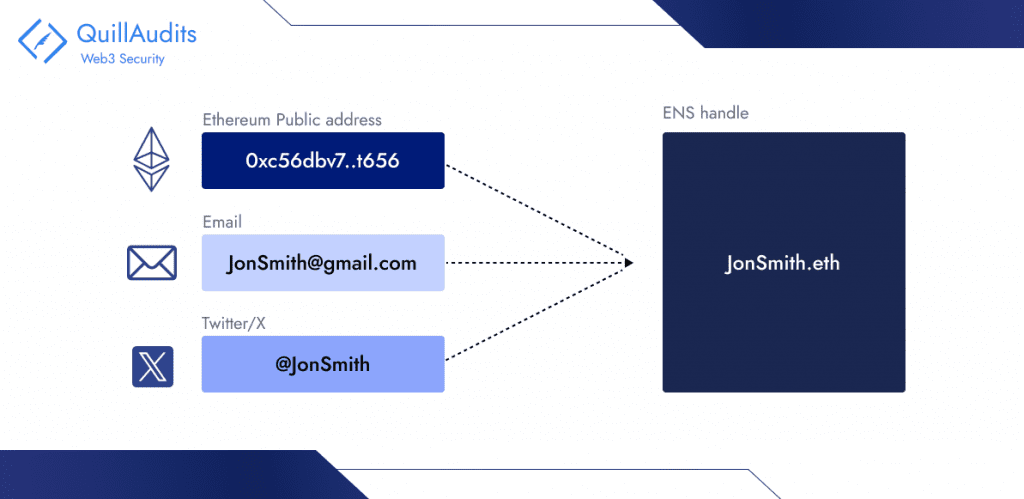
Ethereum Naming Service (ENS), Unstoppable Domains, Lens handle, and several other naming services offer ways for users to add human-readable names to their public addresses. These services create a simplified and human-centric Web3 experience, because public addresses can be difficult to remember and share.
ENS is a naming system based on the Ethereum blockchain that enables users to represent their 42-character Ethereum public address using their ENS name. For instance, Jane Smith can create custom ENS identities to represent her personal and professional life. ENS not only encompasses Ethereum public addresses but it can also encompass addresses of several blockchains, Twitter handles, website URLs, email addresses, and Discord handles.


Identity Attributes
Identity attributes are facts and data points about an individual and/or entity that contribute to ‘who they are’. The degree you earned, the school you went to, and the company you work at are all examples of identity attributes. They are attestations to a given fact or set of facts. SBTs, proposed by Vitalik Buterin, represent digital identity attributes on the Ethereum blockchain.
Reputation
Another key factor in what makes us who we are is our standing in the world. A person’s online persona, the number of Twitter followers they have – the conferences they have attended, the fact that they were early adopters of some trend – all contribute to a person’s reputation and digital identity. The POAP is one protocol that is commonly used within the Ethereum ecosystem to build an online reputation. POAP aims to create a historical record of a person’s contributions or attendance through NFTs.
Digital Collectibles and Assets
People traditionally express themselves through personal belongings and associations, but in the digital world, NFTs allow for unique self-expression. NFTs represent digital or real-world items and are owned and viewed within an individual’s wallet using the Ethereum ecosystem. Owning NFTs reflects interests and contributes to a unique digital identity. For example, JaneSmith.eth may own NFTs like digital art, in-game items, membership NFTs, and PFPs, representing her interests and passions.
The Vital Role of UIDs in Web3
Unique Identifiers (UIDs) are pivotal for web3, acting as foundational components for a range of critical functionalities, all while ensuring the decentralized ecosystem remains secure and efficient. Here’s a deeper look into their importance, stripped of AI-centric language:
User Authentication and Authorization in Decentralized Applications (dApps)
– Verifying User Identity: UIDs are essential for confirming user identities in a decentralized setting. This process sidesteps the need for traditional, centralized authentication methods, aligning with the decentralized ethos of Web3.
– Controlling Access: UIDs enable dApps to manage who gets access to specific functionalities or information. This is achieved by associating certain privileges with individual UIDs, thereby ensuring that only authorized users can access restricted areas or actions within the dApp.
Asset Ownership and History Tracking
– Validating Asset Ownership: In the domain of Web3, digital assets (like cryptocurrencies or NFTs) are tied to UIDs. This direct association allows for clear verification of who owns what, streamlining transactions and the transfer of ownership.
– Historical Tracking: UIDs facilitate the tracking of an asset’s lifecycle — from its creation to its current status. This feature is especially valuable for items where historical authenticity and origin are crucial to their worth.
Securing and Clarifying Transactions
– Ensuring Transaction Integrity: UIDs contribute to creating secure, immutable records of transactions on the blockchain. They link transactions to specific users, promoting transparency and traceability.
– Automating Through Smart Contracts: UIDs are integral to smart contracts, which automatically execute transactions or actions when predefined conditions are met. UIDs ensure these contracts are securely associated with the correct parties.
Preserving Privacy and Enhancing Security
– Protecting User Privacy: UIDs can be designed to allow users to interact and transact while maintaining their anonymity, a significant shift from traditional systems where user data is centralized and more exposed to breaches.
– Strengthening Security Measures: The combination of UIDs and cryptographic methods enhances the overall security of the Web3 ecosystem. It significantly lowers the risk of identity theft and fraud, as UIDs are safeguarded by cryptographic keys that are exceptionally difficult to compromise.
Decentralized identities give individuals control over their data, allowing them to verify information independently. This keeps browsing private, limits tracking, and lets users choose what to share and with whom. Once set up, a decentralized identity cannot be taken away. It also prevents unauthorized sharing of personal data.
Frequent cybersecurity incidents emphasize the necessity of a system to combat phishing, malware infections, and spying, with Verizon reporting that phishing is behind 80% of malware cases and nearly all espionage attempts. Facebook’s numerous data breaches, including one that exposed 540 million records, highlight the risks of centralized data management.
In decentralized identity systems, cryptographic keys replace passwords for secure authentication, improving privacy and security.
Common Web3 Hacks Exploiting UIDs
Sybil Attack
A Sybil Attack involves creating multiple fake identities on a blockchain for harmful purposes. The name “Sybil” comes from a book by Flora Schreiber about a character with multiple personalities, reflecting the attack’s use of numerous identities.
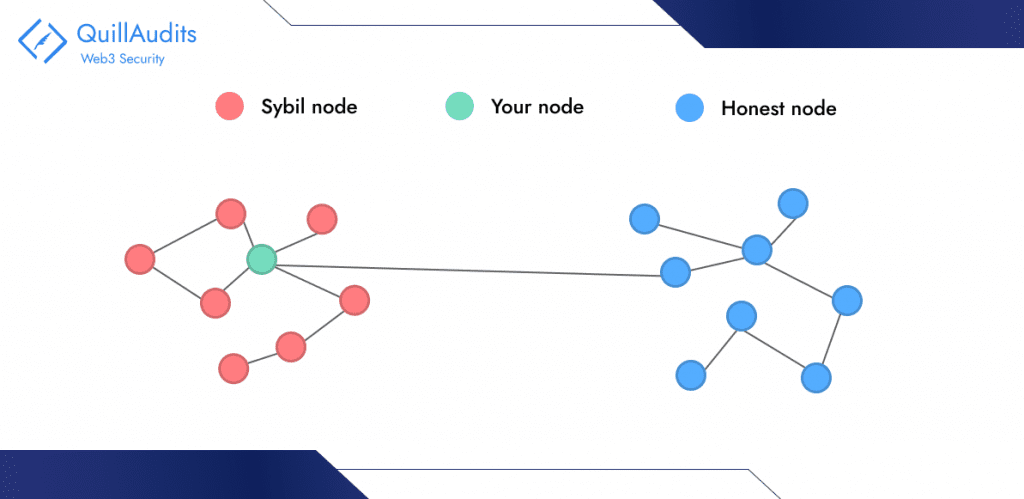


An example of this attack occurred in 2014 when the Tor network, designed for secure communication, was targeted. The attackers sought to reveal the locations and identities of specific Tor users. The Tor team’s investigation revealed that the attack involved controlling about 115 network relays from a single IP address, granting the attacker significant control and access to sensitive information.
Identity Theft
Linking a user’s on-chain address to their off-chain identity can compromise privacy and security. For instance, a hacker traced transactions from a well-known individual’s public cryptocurrency wallet to their personal accounts, breaching personal data and risking financial assets. This incident also made them a target for cyber-attacks and physical threats, emphasizing the critical need to maintain anonymity between digital and real-world personas.
Phishing Attack
Phishing attacks exploit users’ trust in legitimate platforms by creating deceptive websites or dApps that resemble trusted ones. This tricks unsuspecting users into entering sensitive information, leading to unauthorized access. Verifying platforms and remaining vigilant is crucial to prevent such breaches.
Airdrops are promotions where companies distribute free cryptocurrencies to users’ wallets. They have gained popularity among early crypto investors due to the lure of free assets and FOMO (fear of missing out).
Front-running Attacks
Some people use tricks to manipulate the cryptocurrency market, like peeking at cards in a game. In the digital world of blockchain, they look at the public ledger to find patterns in how people make transactions. This helps them predict what transactions users will make in the future. With this knowledge, they strategically place their own transactions to benefit from the way the blockchain processes them.
Double Spending Attacks
Double-spending attacks are a big threat to the security of digital assets. They exploit weaknesses in unique identifiers (UIDs) that indicate ownership. In the digital realm, double-spending allows attackers to duplicate a UID, spending the same asset in two transactions. Blockchain allows changes to transaction data under specific conditions, letting modified blocks be added. If this happens, the one who made the change can recover spent coins.
Mitigating Risks: Enhancing UID Security
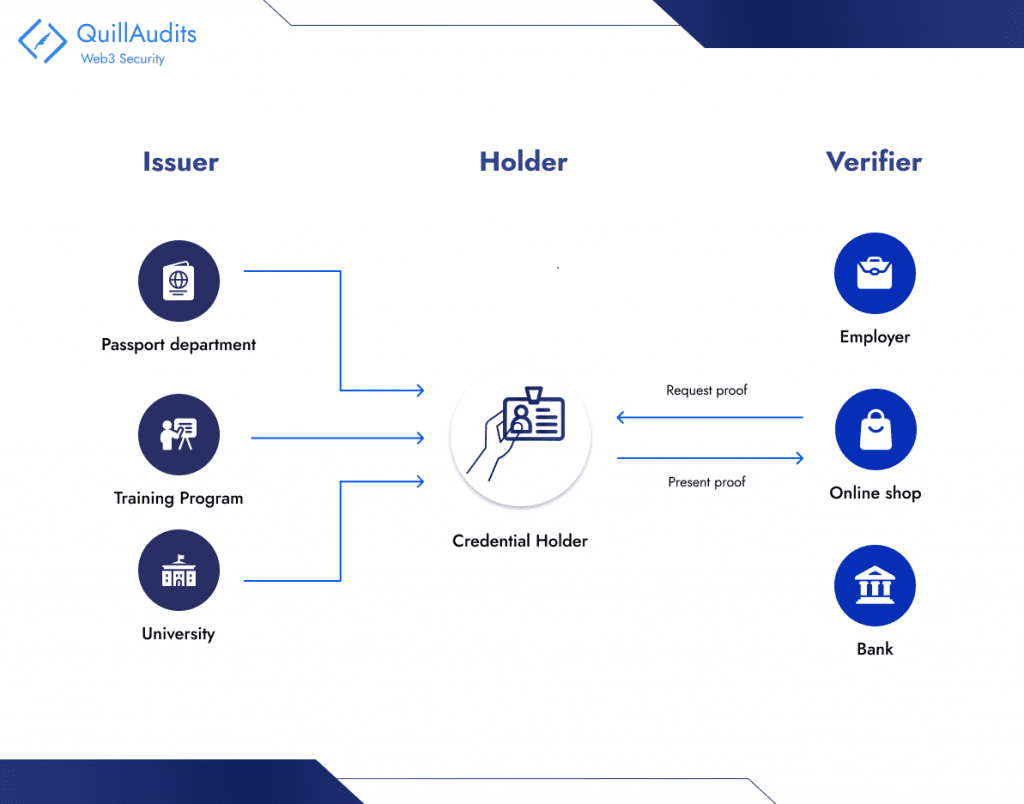
- Self-Sovereign Identity (SSI) allows individuals to control their digital identities directly, bypassing centralized systems. Users manage their data, such as usernames and passwords, through decentralized identifiers in digital wallets. The SSI model involves Holders (the individuals), Issuers (entities granting credentials), and Verifiers (entities validating credentials), promoting autonomy and privacy in digital interactions.


- Zero Knowledge Proofs :- Zero-knowledge proofs allow one party to prove a statement to another without revealing additional information. In the context of UIDs in Web3, ZKPs can be used to authenticate users or prove ownership of an asset or access rights without revealing the UID itself. This ensures that even if the communication is intercepted, the actual UIDs remain secure. ZKPs are not just theoretical; they are being actively implemented in various blockchain projects to enhance privacy and security.
- Strong Authentication with Privacy Technologies:- To secure digital identities, combining multi-factor authentication (MFA) with privacy technologies like homomorphic encryption is key. MFA prevents unauthorized access by requiring multiple proofs of identity, such as passwords and biometrics. Privacy technologies ensure data can be safely analyzed without exposing sensitive information, maintaining user privacy. This approach provides robust protection for digital identities and data.
Conclusion
In conclusion, the evolution of digital identities through Web3 and the use of Unique Identifiers (UIDs) represent a transformative shift in how we navigate the digital realm.UIDs are vital in decentralized ecosystems, enabling secure user interactions, transactions, and safeguarding privacy. The challenges posed by vulnerabilities and potential exploits highlight the imperative for robust security measures and innovative solutions like Self-Sovereign Identity (SSI), Zero-Knowledge Proofs (ZKPs), and enhanced authentication protocols to safeguard these digital beacons.
FAQs
- What are SBTs ?
SBTs or Soulbound tokens are non-transferable tokens that represent a person’s characteristics, features, traits, and achievements. They are ideal for digitally representing assets that cannot be acquired by purchasing, such as certificates of competence, reputation, medical records, etc.
- What is a POAP?
The Proof of Attendance Protocol (POAP) uses blockchain technology to generate digital badges or collectibles. Although the protocol name is the source of the acronym, POAP is also used to refer to the collectibles themselves.
- What is Multifactor authentication or MF?
When logging into your account, MFA adds an additional layer of security by confirming your identity. You need to supply two or more distinct backup factors in order to guarantee ownership.






















